The is the next post in this little Rancher series. After we installed a single node RKE cluster and extended this configurtation to three nodes we will finally install Rancher in this post.
As Rancher is installed with Helm we need to install that first:
rancher@rancher1:~$ wget https://get.helm.sh/helm-v3.5.2-linux-amd64.tar.gz
rancher@rancher1:~$ tar axf helm-v3.5.2-linux-amd64.tar.gz
rancher@rancher1:~$ sudo mv linux-amd64/helm /usr/local/bin/
rancher@rancher1:~$ sudo chown rancher:rancher /usr/local/bin/helm
rancher@rancher1:~$ sudo chmod 770 /usr/local/bin/helm
rancher@rancher1:~$ helm version
WARNING: Kubernetes configuration file is group-readable. This is insecure. Location: kube_config_cluster.yml
version.BuildInfo{Version:"v3.5.2", GitCommit:"167aac70832d3a384f65f9745335e9fb40169dc2", GitTreeState:"dirty", GoVersion:"go1.15.7"}
rancher@rancher1:~$ chmod 700 kube_config_cluster.yml
rancher@rancher1:~$ helm version
version.BuildInfo{Version:"v3.5.2", GitCommit:"167aac70832d3a384f65f9745335e9fb40169dc2", GitTreeState:"dirty", GoVersion:"go1.15.7"}
The namespace for Ranger is “cattle-system” so we need to create it:
rancher@rancher1:~$ kubectl create namespace cattle-system namespace/cattle-system created rancher@rancher1:~$ kubectl get namespace NAME STATUS AGE cattle-system Active 23s default Active 5m25s ingress-nginx Active 4m38s kube-node-lease Active 5m27s kube-public Active 5m27s kube-system Active 5m27s
When it comes to certificates with Ranger you have three options:
- Rancher Generated Certificates (Default)
- Let’s Encrypt
- Certificates from Files
As this envronment is just for demo purposes we’ll be using the default, which is a self signed certificate. For this to work we need to install cert-manager:
rancher@rancher1:~$ kubectl apply --validate=false -f https://github.com/jetstack/cert-manager/releases/download/v1.0.4/cert-manager.crds.yaml customresourcedefinition.apiextensions.k8s.io/certificaterequests.cert-manager.io created customresourcedefinition.apiextensions.k8s.io/certificates.cert-manager.io created customresourcedefinition.apiextensions.k8s.io/challenges.acme.cert-manager.io created customresourcedefinition.apiextensions.k8s.io/clusterissuers.cert-manager.io created customresourcedefinition.apiextensions.k8s.io/issuers.cert-manager.io created customresourcedefinition.apiextensions.k8s.io/orders.acme.cert-manager.io created rancher@rancher1:~$ kubectl create namespace cert-manager namespace/cert-manager created rancher@rancher1:~$ helm repo add jetstack https://charts.jetstack.io WARNING: Kubernetes configuration file is group-readable. This is insecure. Location: /home/rancher/kube_config_cluster.yml "jetstack" has been added to your repositories rancher@rancher1:~$ helm repo update WARNING: Kubernetes configuration file is group-readable. This is insecure. Location: /home/rancher/kube_config_cluster.yml Hang tight while we grab the latest from your chart repositories... ...Successfully got an update from the "jetstack" chart repository ...Successfully got an update from the "rancher-stable" chart repository Update Complete. ⎈Happy Helming!⎈ rancher@rancher1:~$ helm install cert-manager jetstack/cert-manager --namespace cert-manager --version v1.0.4 WARNING: Kubernetes configuration file is group-readable. This is insecure. Location: /home/rancher/kube_config_cluster.yml NAME: cert-manager LAST DEPLOYED: Tue Mar 9 10:05:10 2021 NAMESPACE: cert-manager STATUS: deployed REVISION: 1 TEST SUITE: None NOTES: cert-manager has been deployed successfully! In order to begin issuing certificates, you will need to set up a ClusterIssuer or Issuer resource (for example, by creating a 'letsencrypt-staging' issuer). More information on the different types of issuers and how to configure them can be found in our documentation: https://cert-manager.io/docs/configuration/ For information on how to configure cert-manager to automatically provision Certificates for Ingress resources, take a look at the `ingress-shim` documentation: https://cert-manager.io/docs/usage/ingress/
This deployment can take some, so please monitor the pods until they are ready:
rancher@rancher1:~$ kubectl get pods --namespace cert-manager NAME READY STATUS RESTARTS AGE cert-manager-75dbbd5d6-986cb 1/1 Running 0 49s cert-manager-cainjector-85c559fd6c-td5nh 1/1 Running 0 49s cert-manager-webhook-6c77dfbdb8-wqg9c 1/1 Running 0 49s
For installing Rancher with Helm we need the Rancher repository:
rancher@rancher1:~$ helm repo add rancher-stable https://releases.rancher.com/server-charts/stable "rancher-stable" has been added to your repositories rancher@rancher1:~$ helm repo update Hang tight while we grab the latest from your chart repositories... ...Successfully got an update from the "rancher-stable" chart repository Update Complete. ⎈Happy Helming!⎈
Finally, install Ranger:
rancher@rancher1:~$ helm install rancher rancher-stable/rancher --version v2.5.6 --namespace cattle-system --set hostname=ranger.it.dbi-services.com NAME: rancher LAST DEPLOYED: Tue Mar 9 07:25:23 2021 NAMESPACE: cattle-system STATUS: deployed REVISION: 1 TEST SUITE: None NOTES: Rancher Server has been installed. NOTE: Rancher may take several minutes to fully initialize. Please standby while Certificates are being issued and Ingress comes up. Check out our docs at https://rancher.com/docs/rancher/v2.x/en/ Browse to https://ranger.it.dbi-services.com Happy Containering!
Wait for the deployment to complete:
rancher@rancher1:~$ kubectl get deployments --namespace cattle-system NAME READY UP-TO-DATE AVAILABLE AGE rancher 3/3 3 3 117s
Get the Rancher endpoints:
rancher@rancher1:~$ kubectl -n cattle-system get ep rancher -o wide NAME ENDPOINTS AGE rancher 10.42.0.11:80,10.42.1.9:80,10.42.2.8:80 + 3 more... 51m
Pointing your browser to one of the endpoints should bring you to the Rancher GUI:
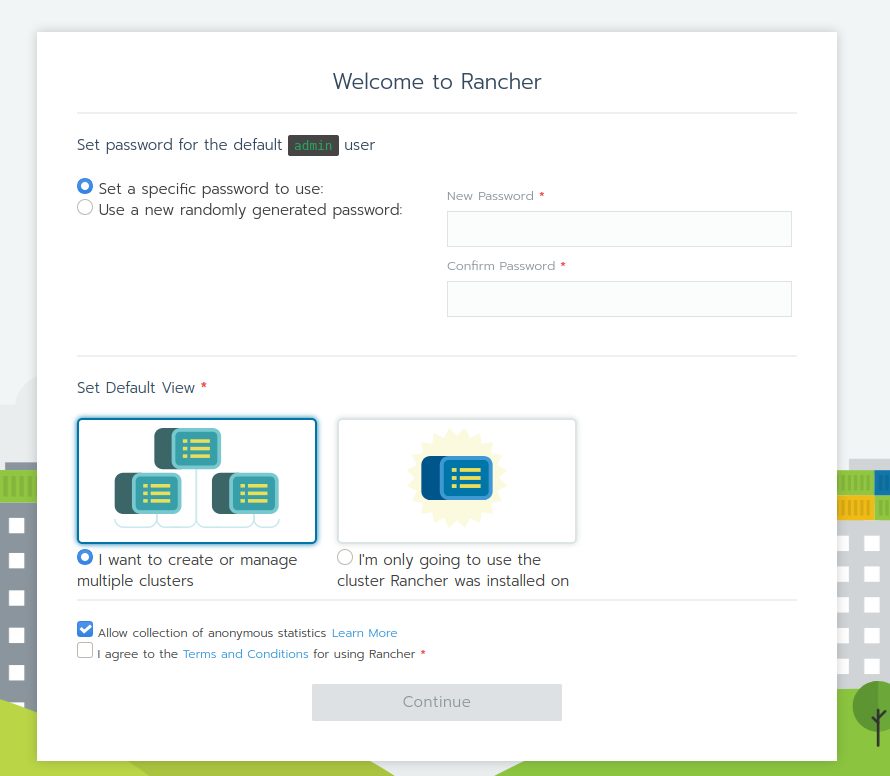
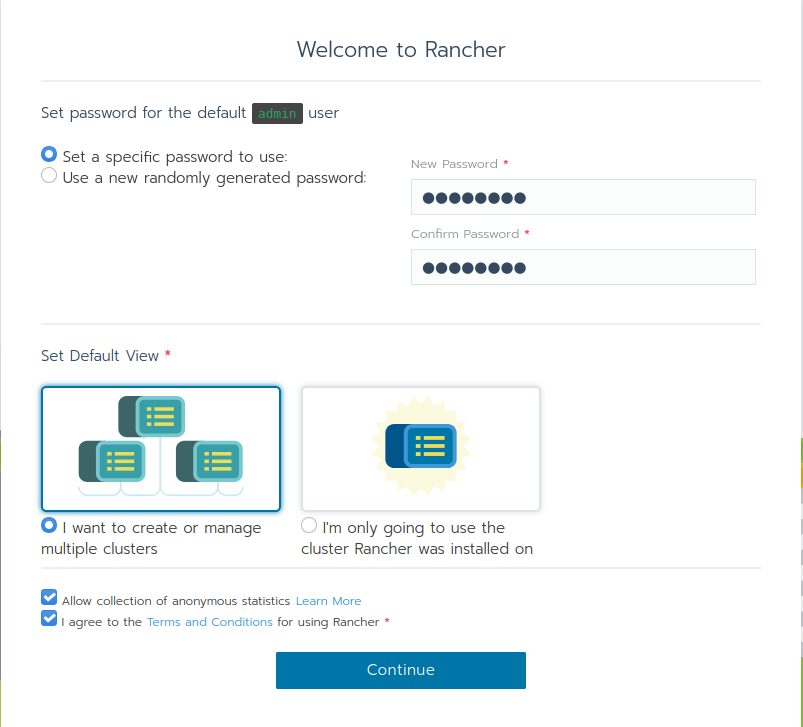
Set your password and options:
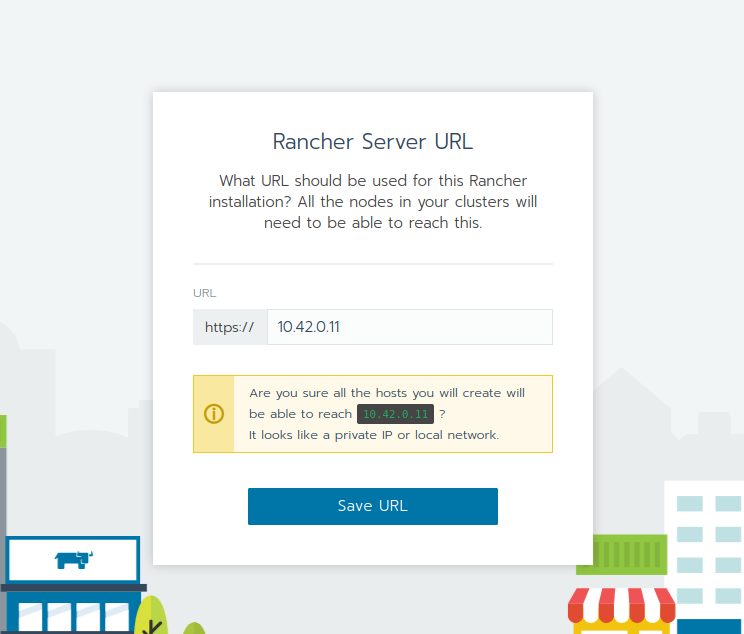
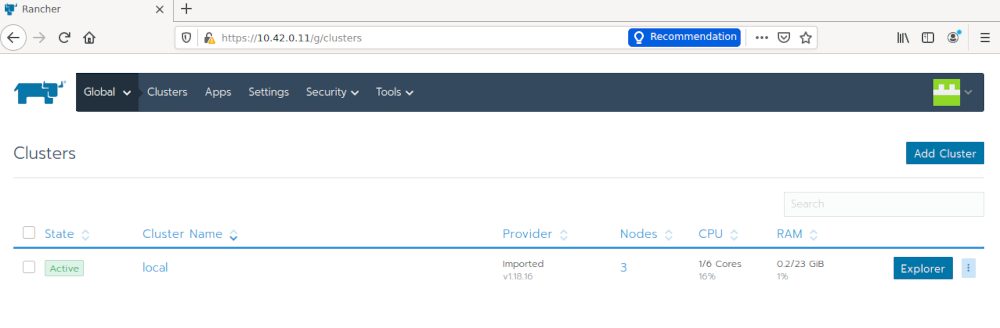
![Thumbnail [60x60]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/DWE_web-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/ENB_web-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/10/JPC_wev-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2023/03/KKE_web-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/OLS_web-min-scaled.jpg)