We’ve finished the last post with a working Compute (Nova) service on the controller and compute node. While only the compute(s) actually run compute resources, Nova is also running on the controller for the management tasks, while libvirt is only running on the compute node. Once more, looking back at what we need at a minimum, we’ve done most of it by now:
- Keystone: Identity service (done)
- Glance: Image service (done)
- Placement: Placement service (done)
- Nova: Compute service (done)
- Neutron: Network service
- Horizon: The OpenStack dashboard
The Network service (Neutron), at least for me, is the hardest part to get right because it requires most of the configuration. As a small refresher, this is the setup we have right now:
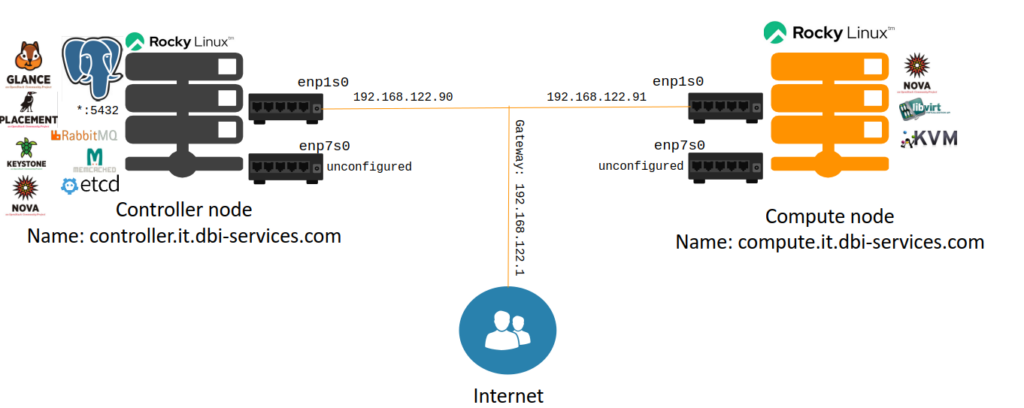
Today, we’re adding the next bit to this: The Network service. Neutron provides “network connectivity as a service” between interfaces, and those are managed by other OpenStack services such as Nova (Compute). You have two choices for implementing this: Provider Networks and Self-service Networks. To keep it as simple as possible for scope of this blog series, we’ll go for a Provider Network.
As with most of the other services, Neutron needs a database:
[root@controller ~]$ su - postgres -c "psql -c \"create user neutron with login password 'admin'\""
CREATE ROLE
[root@controller ~]$ su - postgres -c "psql -c 'create database neutron with owner=neutron'"
CREATE DATABASE
[root@controller ~]$ su - postgres -c "psql -l"
List of databases
Name | Owner | Encoding | Locale Provider | Collate | Ctype | ICU Locale | ICU Rules | Access privileges
------------+-----------+----------+-----------------+-------------+-------------+------------+-----------+-----------------------
glance | glance | UTF8 | libc | en_US.UTF-8 | en_US.UTF-8 | | |
keystone | keystone | UTF8 | libc | en_US.UTF-8 | en_US.UTF-8 | | |
neutron | neutron | UTF8 | libc | en_US.UTF-8 | en_US.UTF-8 | | |
nova | nova | UTF8 | libc | en_US.UTF-8 | en_US.UTF-8 | | |
nova_api | nova | UTF8 | libc | en_US.UTF-8 | en_US.UTF-8 | | |
nova_cell0 | nova | UTF8 | libc | en_US.UTF-8 | en_US.UTF-8 | | |
placement | placement | UTF8 | libc | en_US.UTF-8 | en_US.UTF-8 | | |
postgres | postgres | UTF8 | libc | en_US.UTF-8 | en_US.UTF-8 | | |
template0 | postgres | UTF8 | libc | en_US.UTF-8 | en_US.UTF-8 | | | =c/postgres +
| | | | | | | | postgres=CTc/postgres
template1 | postgres | UTF8 | libc | en_US.UTF-8 | en_US.UTF-8 | | | =c/postgres +
| | | | | | | | postgres=CTc/postgres
(10 rows)
As with most of the other services, we need to install the packages, setup the service, create credentials and API endpoints. For the packages, this is what we need on the controller node:
[root@controller ~]$ dnf install openstack-neutron openstack-neutron-ml2 openstack-neutron-openvswitch -y
For the service, credentials and API endpoints it is more or less the same as for the other services:
[root@controller ~]$ openstack user create --domain default --password-prompt neutron
User Password:
Repeat User Password:
No password was supplied, authentication will fail when a user does not have a password.
+---------------------+----------------------------------+
| Field | Value |
+---------------------+----------------------------------+
| default_project_id | None |
| domain_id | default |
| email | None |
| enabled | True |
| id | 9c9c6e6b622a4e31a176636f4ac0d8d3 |
| name | neutron |
| description | None |
| password_expires_at | None |
+---------------------+----------------------------------+
[root@controller ~]$ openstack role add --project service --user neutron admin
[root@controller ~]$ openstack service create --name neutron --description "OpenStack Networking" network
+-------------+----------------------------------+
| Field | Value |
+-------------+----------------------------------+
| id | 870999a2fb914fe4b9fd8a24a330215f |
| name | neutron |
| type | network |
| enabled | True |
| description | OpenStack Networking |
+-------------+----------------------------------+
[root@controller ~]$ openstack endpoint create --region RegionOne network public http://controller:9696
+--------------+----------------------------------+
| Field | Value |
+--------------+----------------------------------+
| enabled | True |
| id | fb73d8b1db254fea9e4e12f61f4316a3 |
| interface | public |
| region | RegionOne |
| region_id | RegionOne |
| service_id | 870999a2fb914fe4b9fd8a24a330215f |
| service_name | neutron |
| service_type | network |
| url | http://controller:9696 |
[root@controller ~]$ openstack endpoint create --region RegionOne network internal http://controller:9696
+--------------+----------------------------------+
| Field | Value |
+--------------+----------------------------------+
| enabled | True |
| id | c5a7982953e44ea0b612488bebbb88d8 |
| interface | internal |
| region | RegionOne |
| region_id | RegionOne |
| service_id | 870999a2fb914fe4b9fd8a24a330215f |
| service_name | neutron |
| service_type | network |
| url | http://controller:9696 |
+--------------+----------------------------------+
[root@controller ~]$ openstack endpoint create --region RegionOne network admin http://controller:9696
+--------------+----------------------------------+
| Field | Value |
+--------------+----------------------------------+
| enabled | True |
| id | ed9b1e2ebf8b4c7daa9b944b710b8ade |
| interface | admin |
| region | RegionOne |
| region_id | RegionOne |
| service_id | 870999a2fb914fe4b9fd8a24a330215f |
| service_name | neutron |
| service_type | network |
| url | http://controller:9696 |
+--------------+----------------------------------+
Neutron is one of the services which needs configuration on the controller and the compute nodes. For the controller, this is what we need (more on what that all means in a later post when we’ll go into the details):
[root@controller ~]$ egrep -v "^#|^$" /etc/neutron/neutron.conf
[DEFAULT]
auth_strategy = keystone
core_plugin = ml2
service_plugins =
notify_nova_on_port_status_changes = true
notify_nova_on_port_data_changes = true
dhcp_agents_per_network = 2
transport_url = rabbit://openstack:admin@controller:5672/
[agent]
root_helper = sudo neutron-rootwrap /etc/neutron/rootwrap.conf
use_helper_for_ns_read = true
root_helper_daemon = sudo neutron-rootwrap-daemon /etc/neutron/rootwrap.conf
[cache]
[cors]
[database]
backend = postgresql
connection=postgresql+psycopg2://neutron:admin@localhost/neutron
[designate]
[experimental]
[healthcheck]
[ironic]
[keystone_authtoken]
ww_authenticate_uri = http://controller:5000/
auth_url = http://controller:5000/
memcached_servers = controller:11211
auth_type = password
project_domain_name = Default
user_domain_name = Default
project_name = service
username = neutron
password = admin
[nova]
www_authenticate_uri = http://controller:5000/
auth_url = http://controller:5000/
memcached_servers = controller:11211
auth_type = password
project_domain_name = Default
user_domain_name = Default
region_name = RegionOne
project_name = service
username = nova
password = admin
[oslo_concurrency]
lock_path = /var/lib/neutron/tmp
[oslo_messaging_amqp]
[oslo_messaging_kafka]
[oslo_messaging_notifications]
[oslo_messaging_rabbit]
[oslo_middleware]
[oslo_policy]
[oslo_reports]
[oslo_versionedobjects]
[placement]
[privsep]
[profiler]
[profiler_jaeger]
[profiler_otlp]
[quotas]
Configure the Modular Layer 2 (ML2) plugin on the controller node:
[root@controller ~]$ egrep -v "^#|^$" /etc/neutron/plugins/ml2/ml2_conf.ini
[DEFAULT]
[ml2]
type_drivers = flat,vlan
tenant_network_types =
mechanism_drivers = openvswitch
extension_drivers = port_security
[ml2_type_flat]
flat_networks = provider
[ml2_type_geneve]
[ml2_type_gre]
[ml2_type_vlan]
network_vlan_ranges = provider
[ml2_type_vxlan]
[ovn]
[ovn_nb_global]
[ovs]
[ovs_driver]
[securitygroup]
[sriov_driver]
Populate the database (as we know this already from the previous services which need the database as a backend):
[root@controller ~]$ /bin/sh -c "neutron-db-manage --config-file /etc/neutron/neutron.conf \
--config-file /etc/neutron/plugins/ml2/ml2_conf.ini upgrade head" neutron
INFO [alembic.runtime.migration] Context impl PostgresqlImpl.
INFO [alembic.runtime.migration] Will assume transactional DDL.
Running upgrade for neutron ...
INFO [alembic.runtime.migration] Context impl PostgresqlImpl.
INFO [alembic.runtime.migration] Will assume transactional DDL.
INFO [alembic.runtime.migration] Running upgrade -> kilo
INFO [alembic.runtime.migration] Running upgrade kilo -> 354db87e3225
INFO [alembic.runtime.migration] Running upgrade 354db87e3225 -> 599c6a226151
...
INFO [alembic.runtime.migration] Running upgrade 97c25b0d2353 -> 2e0d7a8a1586
INFO [alembic.runtime.migration] Running upgrade 2e0d7a8a1586 -> 5c85685d616d
OK
Start the server on the controller node (notice the systemd output for the ovs-vswitchd service):
[root@controller ~]$ systemctl enable neutron-server.service
Created symlink /etc/systemd/system/multi-user.target.wants/neutron-server.service → /usr/lib/systemd/system/neutron-server.service.
[root@controller ~]$ systemctl enable ovs-vswitchd.service
The unit files have no installation config (WantedBy=, RequiredBy=, Also=,
Alias= settings in the [Install] section, and DefaultInstance= for template
units). This means they are not meant to be enabled or disabled using systemctl.
Possible reasons for having this kind of units are:
• A unit may be statically enabled by being symlinked from another unit's
.wants/ or .requires/ directory.
• A unit's purpose may be to act as a helper for some other unit which has
a requirement dependency on it.
• A unit may be started when needed via activation (socket, path, timer,
D-Bus, udev, scripted systemctl call, ...).
• In case of template units, the unit is meant to be enabled with some
instance name specified.
[root@controller ~]$ ln -s /etc/neutron/plugins/ml2/ml2_conf.ini /etc/neutron/plugin.ini
[root@controller ~]$ systemctl start neutron-server.service
[root@controller ~]$ systemctl start ovs-vswitchd.service
You may already have noticed that Open vSwitch is somehow used here. Now is the time to configure this:
[root@controller ~]$ egrep -v "^#|^$" /etc/neutron/plugins/ml2/openvswitch_agent.ini
[DEFAULT]
[agent]
[dhcp]
[metadata]
[network_log]
[ovs]
bridge_mappings = provider:br-provider
ovsdb_connection = tcp:127.0.0.1:6641
[securitygroup]
enable_security_group = true
firewall_driver = openvswitch
Have a close look at the bridge_mappings parameter, because this defines the bridge we’re going to create right now, and this is where the second interface (enp7s0) on the nodes comes into the game:
[root@controller ~]$ ovs-vsctl add-br br-provider
[root@controller ~]$ ovs-vsctl add-port br-provider enp7s0
[root@controller ~]$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:38:00:73 brd ff:ff:ff:ff:ff:ff
inet 192.168.122.90/24 brd 192.168.122.255 scope global noprefixroute enp1s0
valid_lft forever preferred_lft forever
inet6 fe80::5054:ff:fe38:73/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master ovs-system state UP group default qlen 1000
link/ether 52:54:00:81:1d:26 brd ff:ff:ff:ff:ff:ff
inet6 fe80::9f14:4737:4cf7:d88f/64 scope link noprefixroute
valid_lft forever preferred_lft forever
4: ovs-system: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether aa:e4:50:d2:36:f9 brd ff:ff:ff:ff:ff:ff
5: br-provider: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether fe:84:3e:98:e4:45 brd ff:ff:ff:ff:ff:ff
Set the controller and the manager for the “br-provider” bridge:
[root@controller ~]$ ovs-vsctl set-controller br-provider ptcp:6640
[root@controller ~]$ ovs-vsctl set-manager ptcp:6641
[root@controller ~]$ ovs-vsctl show
a60d818d-3738-4c8e-a9ce-40b84163b14e
Manager "tcp:localhost:6641"
Bridge br-provider
Controller "ptcp:6640"
Port enp7s0
Interface enp7s0
Port br-provider
Interface br-provider
type: internal
ovs_version: "3.3.4-71.el9s"
Because we want the compute nodes later on to get IP addresses by default, we need to configure the DHCP agent on the controller node:
[root@controller ~]$ egrep -v "^#|^$" /etc/neutron/dhcp_agent.ini
[DEFAULT]
interface_driver = openvswitch
dhcp_driver = neutron.agent.linux.dhcp.Dnsmasq
enable_isolated_metadata = true
[agent]
[metadata_rate_limiting]
[ovs]
… and finally the Metadata Agent on the controller node:
[root@controller ~]$ egrep -v "^#|^$" /etc/neutron/metadata_agent.ini
[DEFAULT]
nova_metadata_host = controller
metadata_proxy_shared_secret = admin
[agent]
[cache]
Switching over to the compute node, we must configure Nova (Compute) to use the Networking Service (Neutron). Before we do this, install the required packages on the compute node and configure Open vSwitch in the same way as previously:
[root@compute ~]$ dnf install openstack-neutron openstack-neutron-ml2 openstack-neutron-openvswitch python3-psycopg2 -y
[root@compute ~]$ systemctl start ovs-vswitchd.service
[root@compute ~]$ ovs-vsctl add-br br-provider
[root@compute ~]$ ovs-vsctl add-port br-provider enp7s0
[root@compute ~]$ ovs-vsctl set-manager ptcp:6641
[root@compute ~]$ ovs-vsctl set-controller br-provider ptcp:6640
To configure Nova to use the Neutron, add the “[neutron]” section to “/etc/nova/nova.conf”:
[neutron]
auth_url = http://controller:5000
auth_type = password
project_domain_name = Default
user_domain_name = Default
region_name = RegionOne
project_name = service
username = neutron
password = admin
service_metadata_proxy = true
metadata_proxy_shared_secret = admin
Configure Neutron:
[root@compute ~]$ egrep -v "^#|^$" /etc/neutron/neutron.conf
[DEFAULT]
core_plugin = ml2
auth_strategy = keystone
transport_url = rabbit://openstack:admin@controller
[agent]
root_helper = sudo neutron-rootwrap /etc/neutron/rootwrap.conf
use_helper_for_ns_read = true
root_helper_daemon = sudo neutron-rootwrap-daemon /etc/neutron/rootwrap.conf
[cache]
[cors]
[database]
backend = postgresql
connection=postgresql+psycopg2://neutron:admin@controller/neutron
[designate]
[experimental]
[healthcheck]
[ironic]
[keystone_authtoken]
www_authenticate_uri = http://controller:5000/
auth_url = http://controller:5000/
memcached_servers = controller:11211
auth_type = password
project_domain_name = Default
user_domain_name = Default
project_name = service
username = neutron
password = admin
[nova]
www_authenticate_uri = http://controller:5000/
auth_url = http://controller:5000/
memcached_servers = controller:11211
auth_type = password
project_domain_name = Default
user_domain_name = Default
region_name = RegionOne
project_name = service
username = nova
password = admin
[oslo_concurrency]
[oslo_messaging_amqp]
[oslo_messaging_kafka]
[oslo_messaging_notifications]
[oslo_messaging_rabbit]
[oslo_middleware]
[oslo_policy]
[oslo_reports]
[oslo_versionedobjects]
[placement]
[privsep]
[profiler]
[profiler_jaeger]
[profiler_otlp]
[quotas]
[ssl]
… and the Open vSwitch agent:
[root@compute ~]$ egrep -v "^#|^$" /etc/neutron/plugins/ml2/openvswitch_agent.ini
[DEFAULT]
[agent]
[dhcp]
[metadata]
[network_log]
[ovs]
bridge_mappings = provider:br-provider
ovsdb_connection = tcp:127.0.0.1:6641
[securitygroup]
firewall_driver =
… and the Metadata Agent:
[root@compute ~]$ egrep -v "^#|^$" /etc/neutron/metadata_agent.ini
[DEFAULT]
nova_metadata_host = controller
metadata_proxy_shared_secret = admin
[agent]
[cache]
[root@compute ~]$ ln -s /etc/neutron/plugins/ml2/ml2_conf.ini /etc/neutron/plugin.in
Start the services on the controller and the compute nodes:
# controller
[root@controller ~]$ systemctl enable neutron-server.service \
neutron-openvswitch-agent.service neutron-dhcp-agent.service \
neutron-metadata-agent.service
Created symlink /etc/systemd/system/multi-user.target.wants/neutron-openvswitch-agent.service → /usr/lib/systemd/system/neutron-openvswitch-agent.service.
Created symlink /etc/systemd/system/multi-user.target.wants/neutron-dhcp-agent.service → /usr/lib/systemd/system/neutron-dhcp-agent.service.
Created symlink /etc/systemd/system/multi-user.target.wants/neutron-metadata-agent.service → /usr/lib/systemd/system/neutron-metadata-agent.service.
# compute
[root@compute ~]$ systemctl enable neutron-server.service \
neutron-openvswitch-agent.service \
neutron-metadata-agent.service
Created symlink /etc/systemd/system/multi-user.target.wants/neutron-server.service → /usr/lib/systemd/system/neutron-server.service.
Created symlink /etc/systemd/system/multi-user.target.wants/neutron-openvswitch-agent.service → /usr/lib/systemd/system/neutron-openvswitch-agent.service.
Created symlink /etc/systemd/system/multi-user.target.wants/neutron-metadata-agent.service → /usr/lib/systemd/system/neutron-metadata-agent.service.
# controller
[root@controller ~]$ systemctl start neutron-server.service \
neutron-openvswitch-agent.service neutron-dhcp-agent.service \
neutron-metadata-agent.service
# compute
[root@compute ~]$ systemctl start neutron-server.service \
neutron-openvswitch-agent.service \
neutron-metadata-agent.service
Done with that we need to create the network we want to use on the controller node (adapt the network to your own setup):
[root@controller ~]$ openstack network create --share --external \
--provider-physical-network provider \
--provider-network-type flat provider
+---------------------------+--------------------------------------+
| Field | Value |
+---------------------------+--------------------------------------+
| admin_state_up | UP |
| availability_zone_hints | |
| availability_zones | |
| created_at | 2025-01-22T13:25:21Z |
| description | |
| dns_domain | None |
| id | aa8bd4f9-4d89-4c7f-803c-c56aaf8f8f57 |
| ipv4_address_scope | None |
| ipv6_address_scope | None |
| is_default | None |
| is_vlan_transparent | None |
| mtu | 1500 |
| name | provider |
| port_security_enabled | True |
| project_id | 920bf34a6c88454f90d405124ca1076d |
| provider:network_type | flat |
| provider:physical_network | provider |
| provider:segmentation_id | None |
| qos_policy_id | None |
| revision_number | 1 |
| router:external | External |
| segments | None |
| shared | True |
| status | ACTIVE |
| subnets | |
| tags | |
| updated_at | 2025-01-22T13:25:21Z |
+---------------------------+--------------------------------------+
[root@controller ~]$ openstack subnet create --network provider \
--allocation-pool start=10.0.0.101,end=10.0.0.250 \
--dns-nameserver 8.8.4.4 --gateway 10.0.0.1 \
--subnet-range 10.0.0.0/24 provider
+----------------------+--------------------------------------+
| Field | Value |
+----------------------+--------------------------------------+
| allocation_pools | 10.0.0.101-10.0.0.250 |
| cidr | 10.0.0.0/24 |
| created_at | 2025-01-22T13:25:54Z |
| description | |
| dns_nameservers | 8.8.4.4 |
| dns_publish_fixed_ip | None |
| enable_dhcp | True |
| gateway_ip | 10.0.0.1 |
| host_routes | |
| id | 77ba8f00-edeb-4555-8c2a-be48b24f0320 |
| ip_version | 4 |
| ipv6_address_mode | None |
| ipv6_ra_mode | None |
| name | provider |
| network_id | aa8bd4f9-4d89-4c7f-803c-c56aaf8f8f57 |
| project_id | 920bf34a6c88454f90d405124ca1076d |
| revision_number | 0 |
| router:external | True |
| segment_id | None |
| service_types | |
| subnetpool_id | None |
| tags | |
| updated_at | 2025-01-22T13:25:54Z |
+----------------------+--------------------------------------+
Finally, verify that everything is working as expected:
[root@controller ~]$ openstack extension list --network
+-----------------------------------------------------------+---------------------------------------------+-----------------------------------------------------------+
| Name | Alias | Description |
+-----------------------------------------------------------+---------------------------------------------+-----------------------------------------------------------+
| Address group | address-group | Support address group |
| Address scope | address-scope | Address scopes extension. |
| agent | agent | The agent management extension. |
| Agent's Resource View Synced to Placement | agent-resources-synced | Stores success/failure of last sync to Placement |
| Allowed Address Pairs | allowed-address-pairs | Provides allowed address pairs |
| Availability Zone | availability_zone | The availability zone extension. |
| Availability Zone Filter Extension | availability_zone_filter | Add filter parameters to AvailabilityZone resource |
| Default Subnetpools | default-subnetpools | Provides ability to mark and use a subnetpool as the |
| | | default. |
| DHCP Agent Scheduler | dhcp_agent_scheduler | Schedule networks among dhcp agents |
| Empty String Filtering Extension | empty-string-filtering | Allow filtering by attributes with empty string value |
| Neutron external network | external-net | Adds external network attribute to network resource. |
| Neutron Extra DHCP options | extra_dhcp_opt | Extra options configuration for DHCP. For example PXE |
| | | boot options to DHCP clients can be specified (e.g. tftp- |
| | | server, server-ip-address, bootfile-name) |
| Filter parameters validation | filter-validation | Provides validation on filter parameters. |
| Neutron Service Flavors | flavors | Flavor specification for Neutron advanced services. |
| IP address substring filtering | ip-substring-filtering | Provides IP address substring filtering when listing |
| | | ports |
| Multi Provider Network | multi-provider | Expose mapping of virtual networks to multiple physical |
| | | networks |
| Network MTU | net-mtu | Provides MTU attribute for a network resource. |
| Network MTU (writable) | net-mtu-writable | Provides a writable MTU attribute for a network resource. |
| Network Availability Zone | network_availability_zone | Availability zone support for network. |
| Network IP Availability | network-ip-availability | Provides IP availability data for each network and |
| | | subnet. |
| Pagination support | pagination | Extension that indicates that pagination is enabled. |
| Port device profile | port-device-profile | Expose the port device profile (Cyborg) |
| Neutron Port MAC address override | port-mac-override | Allow overriding the MAC address of a direct-physical |
| | | Port via the active binding profile |
| Neutron Port MAC address regenerate | port-mac-address-regenerate | Network port MAC address regenerate |
| Port NUMA affinity policy | port-numa-affinity-policy | Expose the port NUMA affinity policy |
| Port NUMA affinity policy "socket" | port-numa-affinity-policy-socket | Adds "socket" to the supported port NUMA affinity |
| | | policies |
| Port Binding | binding | Expose port bindings of a virtual port to external |
| | | application |
| Port Bindings Extended | binding-extended | Expose port bindings of a virtual port to external |
| | | application |
| Port Security | port-security | Provides port security |
| project_id field enabled | project-id | Extension that indicates that project_id field is |
| | | enabled. |
| Provider Network | provider | Expose mapping of virtual networks to physical networks |
| Quota engine limit check | quota-check-limit | Support for checking the resource usage before applying a |
| | | new quota limit |
| Quota management support | quotas | Expose functions for quotas management per project |
| Quota details management support | quota_details | Expose functions for quotas usage statistics per project |
| RBAC Policies | rbac-policies | Allows creation and modification of policies that control |
| | | tenant access to resources. |
| Add address_group type to RBAC | rbac-address-group | Add address_group type to network RBAC |
| Add address_scope type to RBAC | rbac-address-scope | Add address_scope type to RBAC |
| Add security_group type to network RBAC | rbac-security-groups | Add security_group type to network RBAC |
| Add subnetpool type to RBAC | rbac-subnetpool | Add subnetpool type to RBAC |
| If-Match constraints based on revision_number | revision-if-match | Extension indicating that If-Match based on |
| | | revision_number is supported. |
| Resource revision numbers | standard-attr-revisions | This extension will display the revision number of |
| | | neutron resources. |
| Default rules for security groups | security-groups-default-rules | Configure set of security group rules used as default |
| | | rules for every new security group |
| Normalized CIDR field for security group rules | security-groups-normalized-cidr | Add new field with normalized remote_ip_prefix cidr in SG |
| | | rule |
| Port filtering on security groups | port-security-groups-filtering | Provides security groups filtering when listing ports |
| Remote address group id field for security group rules | security-groups-remote-address-group | Add new field of remote address group id in SG rules |
| Security group rule belongs to the project's default | security-groups-rules-belongs-to-default-sg | Flag to determine if the security group rule belongs to |
| security group | | the project's default security group |
| Security group filtering on the shared field | security-groups-shared-filtering | Support filtering security groups on the shared field |
| security-group | security-group | The security groups extension. |
| Neutron Service Type Management | service-type | API for retrieving service providers for Neutron advanced |
| | | services |
| Sorting support | sorting | Extension that indicates that sorting is enabled. |
| standard-attr-description | standard-attr-description | Extension to add descriptions to standard attributes |
| Stateful security group | stateful-security-group | Indicates if the security group is stateful or not |
| Subnet belongs to an external network | subnet-external-network | Informs if the subnet belongs to an external network |
| Subnet Onboard | subnet_onboard | Provides support for onboarding subnets into subnet pools |
| Subnet service types | subnet-service-types | Provides ability to set the subnet service_types field |
| Subnet Allocation | subnet_allocation | Enables allocation of subnets from a subnet pool |
| Subnet Pool Prefix Operations | subnetpool-prefix-ops | Provides support for adjusting the prefix list of subnet |
| | | pools |
| Tag creation extension | tag-creation | Allow to create multiple tags for a resource |
| Tag support for resources with standard attribute: port, | standard-attr-tag | Enables to set tag on resources with standard attribute. |
| subnet, subnetpool, network, security_group, router, | | |
| floatingip, policy, trunk, network_segment_range | | |
| Resource timestamps | standard-attr-timestamp | Adds created_at and updated_at fields to all Neutron |
| | | resources that have Neutron standard attributes. |
+-----------------------------------------------------------+---------------------------------------------+-----------------------------------------------------------+
[root@controller ~]$ openstack network agent list
+--------------------------------------+--------------------+--------------------------------+-------------------+-------+-------+---------------------------+
| ID | Agent Type | Host | Availability Zone | Alive | State | Binary |
+--------------------------------------+--------------------+--------------------------------+-------------------+-------+-------+---------------------------+
| 0fff6416-31eb-4fbd-b8a6-dfd8f52acb6d | DHCP agent | controller.it.dbi-services.com | nova | :-) | UP | neutron-dhcp-agent |
| 2fd7ed1b-d53a-47a5-ad60-9ff95bda4f51 | Metadata agent | controller.it.dbi-services.com | None | :-) | UP | neutron-metadata-agent |
| 7b1b2385-612e-47e8-8f31-dfb78afa0b0b | Metadata agent | compute.it.dbi-services.com | None | :-) | UP | neutron-metadata-agent |
| 7855461f-a5c0-4b90-b52c-d9695b92107d | Open vSwitch agent | controller.it.dbi-services.com | None | :-) | UP | neutron-openvswitch-agent |
| dac53d0d-e24c-4e98-938a-7f480b457486 | Open vSwitch agent | compute.it.dbi-services.com | None | :-) | UP | neutron-openvswitch-agent |
+--------------------------------------+--------------------+--------------------------------+-------------------+-------+-------+---------------------------+
Done. This leaves us with the following components for today:
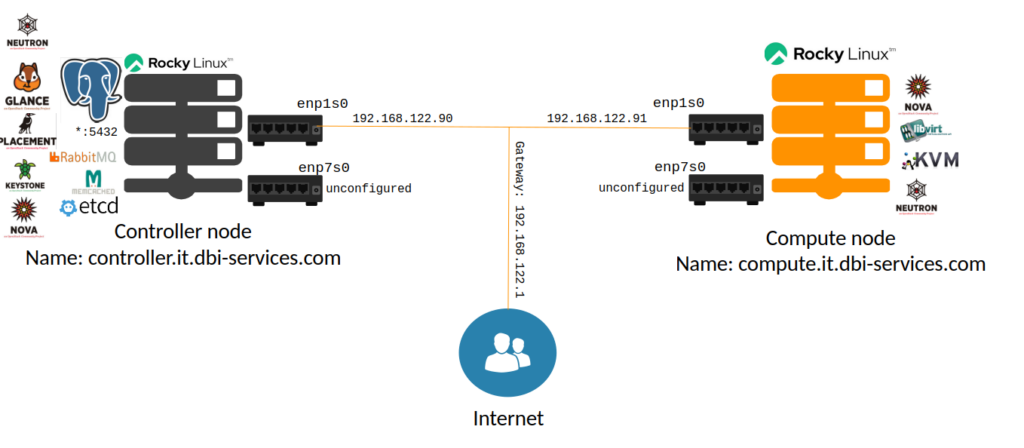
In the next post, we’ll setup the final service for our playground, Horizon (The OpenStack dashboard).
![Thumbnail [60x60]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/DWE_web-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2025/07/ALK_MIN.jpeg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2025/03/OBA_web-scaled.jpg)