One question that comes often out working with Percona Monitoring and Management tool, is how to use LDAP to define users which can connect to the PMM web interface.
Let’s see how to implement this kind of configuration.
As you can read in a previous post where I gave an overview of PMM, the product is based on a client-server model.
You have 4 different ways to install the PMM server:
– via Docker images
– via a Virtual appliance provided by Percona
– on the Amazon AWS Cloud
– using an easy install script which also installs Docker for you.
I’m used to install the PMM server with the first method, following next steps:
1) I pull the last version of PMM server image:
$ sudo docker pull percona/pmm-server:2
2) I create a container for persistent data (pmm-data):
$ sudo docker create -v /srv --name pmm-data percona/pmm-server:2 /bin/true
3) I do the run of the pulled image to start the server (pmm-server):
$ sudo docker run --detach --restart always -p 80:80 -p 443:443 --volumes-from pmm-data --name pmm-server percona/pmm-server:2
I can now connect to the PMM web interface at “https://PMM_server_IP:443″ with the user “admin” (the password is “admin” and should be changed at the first login), which is the user that I use to manage the platform. I have then the choice to create other users which can connect to the console, with 3 different levels of permissions:
– Admin
– Editor
– Viewer
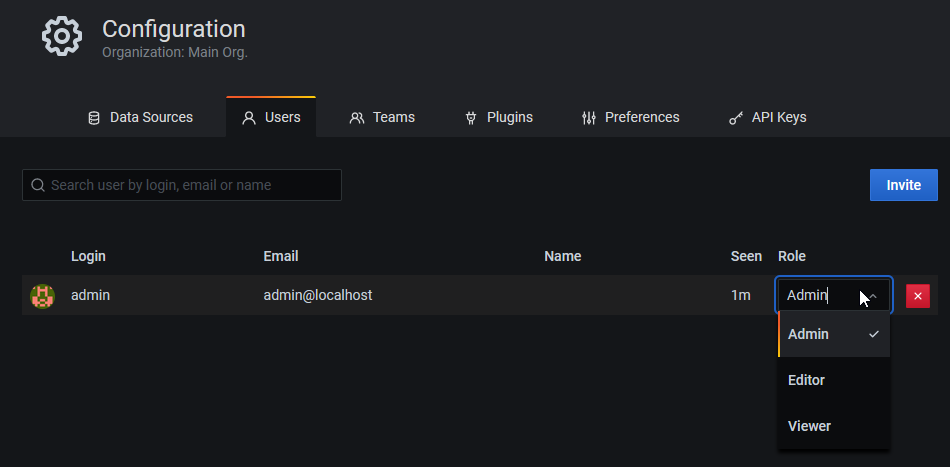
But if you already have an LDAP, you can use it to let users of your organization directly access to PMM platform.
Normally this is done by modifying 2 configuration files of Grafana:
– /etc/grafana/grafana.ini -> to turn on the LDAP option
– /etc/grafana/ldap.toml -> to handle LDAP configuration
and then restarting the Grafana services.
In my case, in order to make these changes persistent to PMM server upgrades and maintenance, I will:
1) Activate LDAP at the run of the container:
$ sudo docker run --detach --restart always -e GF_AUTH_LDAP_CONFIG_FILE=/srv/grafana/ldap.toml -e GF_AUTH_LDAP_ENABLED=true -e GF_AUTH_LDAP_ALLOW_SIGN_UP=true -p 80:80 -p 443:443 --volumes-from pmm-data --name pmm-server percona/pmm-server:2
2) Place the ldap.toml configuration file in the persistent pmm-data container:
$ sudo docker exec -it pmm-server /bin/bash [root@0ea845ff56ec opt]# cp /etc/grafana/ldap.toml /srv/grafana/ldap.toml
Now a new LDAP tab appears on the Server Admin page of the PMM interface:
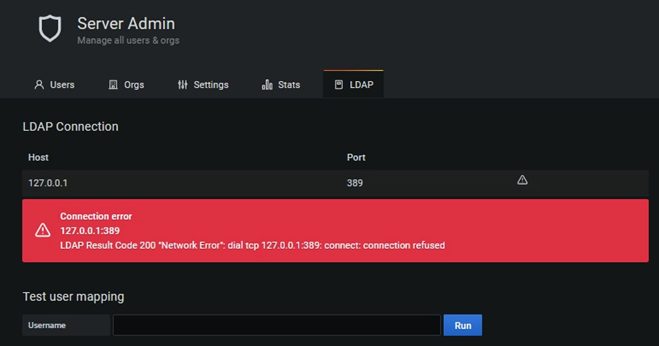
The connection error is normal here, because I still have to adapt the following LDAP configuration (remember, on the persistent volume!):
$ vi /srv/grafana/ldap.toml # To troubleshoot and get more log info enable ldap debug logging in grafana.ini # [log] # filters = ldap:debug [[servers]] # Ldap server host (specify multiple hosts space separated) host = "127.0.0.1" # Default port is 389 or 636 if use_ssl = true port = 389 # Set to true if LDAP server should use an encrypted TLS connection (either with STARTTLS or LDAPS) use_ssl = false # If set to true, use LDAP with STARTTLS instead of LDAPS start_tls = false # set to true if you want to skip ssl cert validation ssl_skip_verify = false # set to the path to your root CA certificate or leave unset to use system defaults # root_ca_cert = "/path/to/certificate.crt" # Authentication against LDAP servers requiring client certificates # client_cert = "/path/to/client.crt" # client_key = "/path/to/client.key" # Search user bind dn bind_dn = "cn=admin,dc=grafana,dc=org" # Search user bind password # If the password contains # or ; you have to wrap it with triple quotes. Ex """#password;""" bind_password = 'grafana' # User search filter, for example "(cn=%s)" or "(sAMAccountName=%s)" or "(uid=%s)" search_filter = "(cn=%s)" # An array of base dns to search through search_base_dns = ["dc=grafana,dc=org"] ## For Posix or LDAP setups that does not support member_of attribute you can define the below settings ## Please check grafana LDAP docs for examples # group_search_filter = "(&(objectClass=posixGroup)(memberUid=%s))" # group_search_base_dns = ["ou=groups,dc=grafana,dc=org"] # group_search_filter_user_attribute = "uid" # Specify names of the ldap attributes your ldap uses [servers.attributes] name = "givenName" surname = "sn" username = "cn" member_of = "memberOf" email = "email" # Map ldap groups to grafana org roles [[servers.group_mappings]] group_dn = "cn=admins,ou=groups,dc=grafana,dc=org" org_role = "Admin" # To make user an instance admin (Grafana Admin) uncomment line below # grafana_admin = true # The Grafana organization database id, optional, if left out the default org (id 1) will be used # org_id = 1 [[servers.group_mappings]] group_dn = "cn=users,ou=groups,dc=grafana,dc=org" org_role = "Editor" [[servers.group_mappings]] # If you want to match all (or no ldap groups) then you can use wildcard group_dn = "*" org_role = "Viewer"
And when I change the configuration to point to my LDAP server, I can test the user mapping:
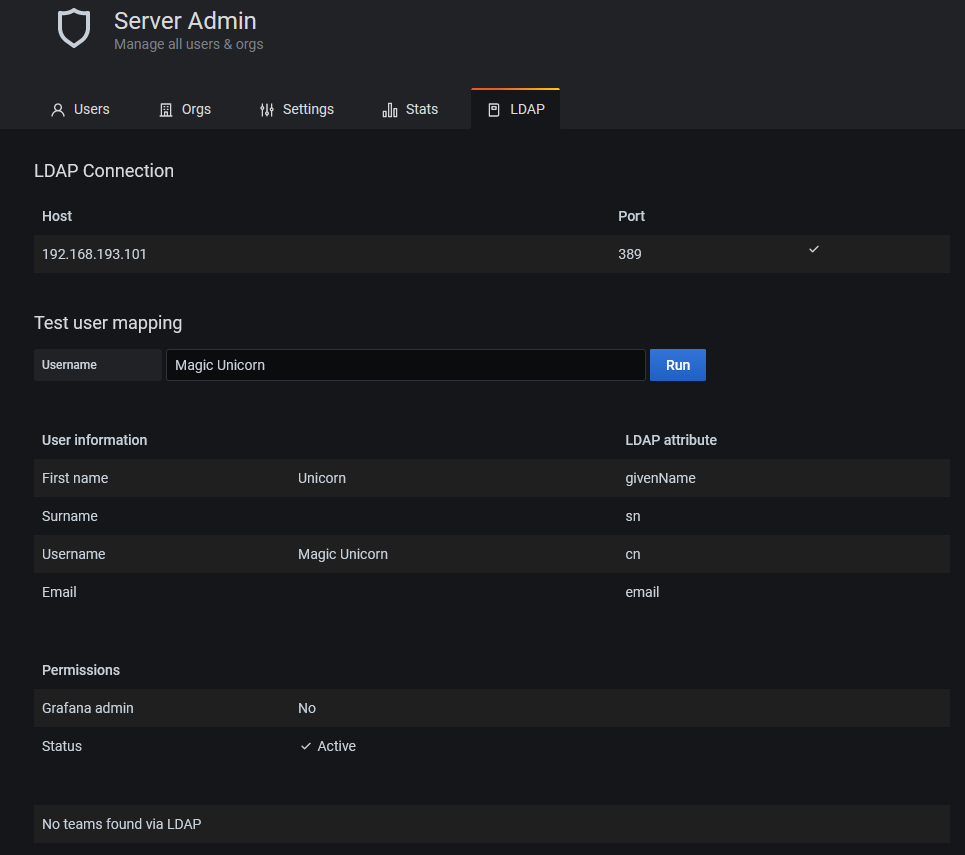
and then directly login with my username which has only Viewer privileges:
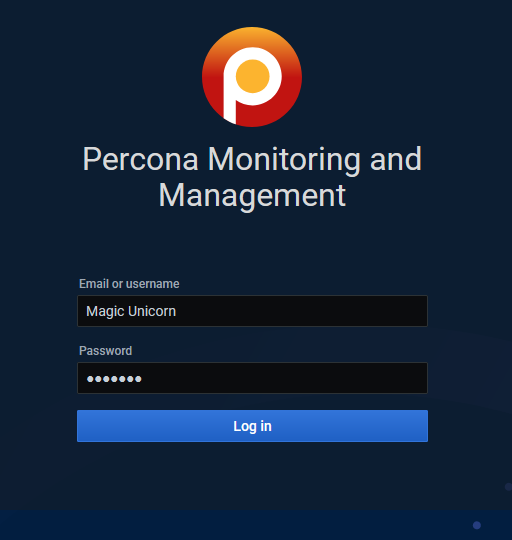
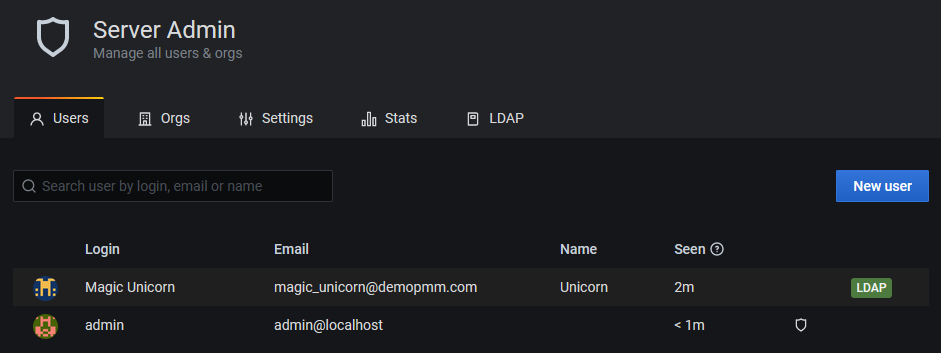
And indeed new user is synced via LDAP:
As usual, stay tuned, other posts about PMM will come soon 😉
By Elisa Usai
![Thumbnail [60x60]](https://www.dbi-services.com/blog/wp-content/uploads/2022/10/ELU_web-min-1-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/10/STS_web-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/STH_web-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/09/SNA_web-min-scaled.jpg)