Introduction & why attaching your personnal network to OCI (Oracle Cloud Infrastructure)
You want to use your existing tools and infrastructure, but you need high internet performance for your Oracle environment – the combination of on premise and OCI may make sense for you. Or if you simply want to check what possibilities OCI provides for your business with OCI, you can gain some experience with a mix of both worlds.
Maybe you are interested in Oracle Cloud Infrastructure and you don’t want to move all of your IT to the cloud? Or you have some tools or data locally in your premise IT you want to user further? If you don’t plan to move terabytes of data you can do a quick and easy test within a short time with an open source firewall from IPFire (https://www.ipfire.org) to connect your infrastructure to OCI via VPN. If you have an existing IPFire firewall connected to the internet (in my case no NAT) the time to configure the needed 2 IPSec tunnels is done in less than 5min.
Why open source ‘IPFire’ Firewall?
I’m using IPFire-firewall since years without problems and even if you’re not very experienced command-line user you can install, configure and maintain the firewall by GUI easily too.
And in addition, regarding our intention to connect OCI, the IPSec configuration is very simple to configure via GUI too.
Example configuration overview
CPE (Customer-Premises Equipment) is nothing else than your personal IT entry-point. So please don’t use public IP-address beginning with something like 94.16.xxx.yyy if you don’t want to run into trouble with my provider Quickline (except if you have the same provider. Only then it would look similar).
/!\ Please check first which IP-address is assigned by your ISP (Internet Service Provider) before you begin to setup CPE in OCI. The OCI CPE is configured together with your personal firewall.
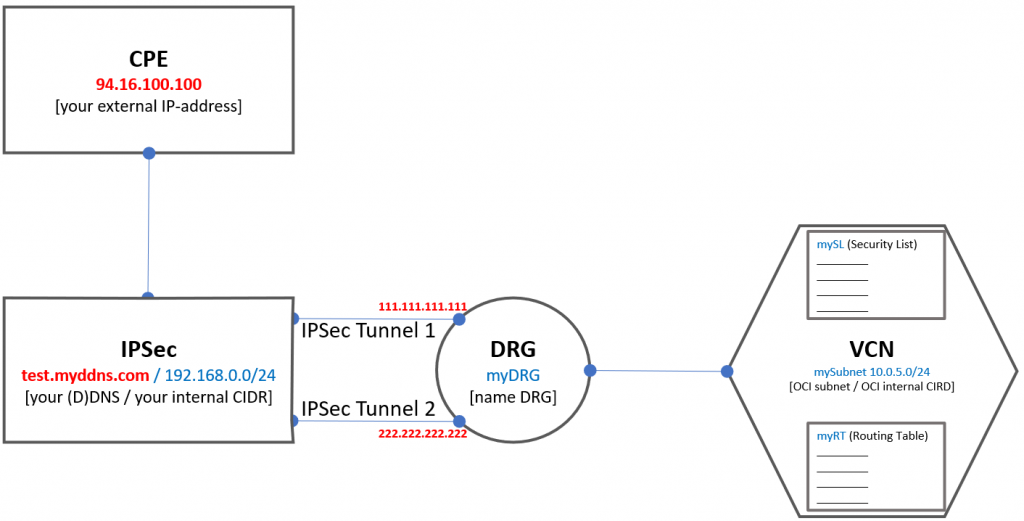
IPSec to be defined on both sides – in OCI and in your personal network (in my example with the IPFire firewall and the IPSec configuration).
DRG “Dynamic Routing Gateway” will coordinate routing between your on-prem netword and the VCNs/Subnets in OCI.
VCN “Virtual Cloud Network” is the network you attach other components to and where you can define subnets, routing tables, security lists.
Attach the Routing Table (RT) and Security List (SL) definitions to your subnets later. I was wondering why it didn’t work on my first attempt.
VCN Subnet – here you place your compute instances and apply your SL (Security List ~firewall rules) and RT (Routing Table).
Prerequisites
On OCI side
- your OCI tenancy
- VCN (Virtual Cloud Network)
- VCN subnet
- CPE (Customer-Premises Equipment)
- IPSec connection
- 2x IPSec tunnel
- Dynamic Routing Gateway (DRG)
- Security List (SL)
- Routing Table (RT)
- At least 1 instance
On customer side
- IPFire firewall
- Your external IP-Address
- 1 LINUX OS instance on your premise IT
Optional
- DDNS for your personal network
- DDNS domain name or your own DNS
Setup OCI
VCN
| Name | myVCN |
| CIDR | 10.0.5.0/24 |
VCN subnet
| Name | mySubnet | |
| CIDR | 10.0.5.0/24 | |
| RT | RouteTableMySubnet | |
| Destination | 192.168.0.0/24 [customers internal CIDR] | |
| Target Type | Dynamic Routing Gateway | |
| Target | myDRG | |
| DRG att | myDRG_Attachment_Subnet | |
| Att Name | myDRG_Attachment_mySubnet | |
| Lifecyc State | Attached | |
| DRG | myDRG | |
| VCN RT | – | |
| Cross-Ten. | No | |
| SL | SecurityListMySubnet | |
| Ingress Rules (1) | ||
| Stateless | No | |
| Source | 192.168.0.0/24 [customers internal CIDR] | |
| IP Protocol | TCP | |
| Source PR | All | |
| Destin. PR | 22 | |
| Type&Code | ||
| Allows | TCP traffic for pots: 22 SSH Remote Login Protocol | |
| Description | myCPE(ingress) |
DRG
| Name | myDRG | |
| Lifecycle St | Available (when at least one tunnel up) | |
| Ora Redund. | Redundant (when all up and running) | |
| VCN att. | (2) | |
| (1/2) | Att Name | DRG_Attachment_for_IPSec_Tunnel: myIPSecTunnel1 |
| Lifecyc St | Attached | |
| IPSec Tun. | myIPSecTunnel1 | |
| DRG RT | Autogen. Drg RT for RPC, VC, and IPSec att. | |
| CPE | myCPE | |
| CPE IKE Id | test.myddns.com (if you changed IPSec ‘IP-Connection’ with FQDN) | |
| (2/2) | Att Name | DRG_Attachment_for_IPSec_Tunnel: myIPSecTunnel2 |
| Lifecyc St | Attached | |
| IPSec Tun. | myIPSecTunnel2 | |
| DRG RT | Autogen. Drg RT for RPC, VC, and IPSec att. | |
| CPE | myCPE | |
| CPE IKE Id | test.myddns.com (if you changed IPSec ‘IP-Connection’ with FQDN) |
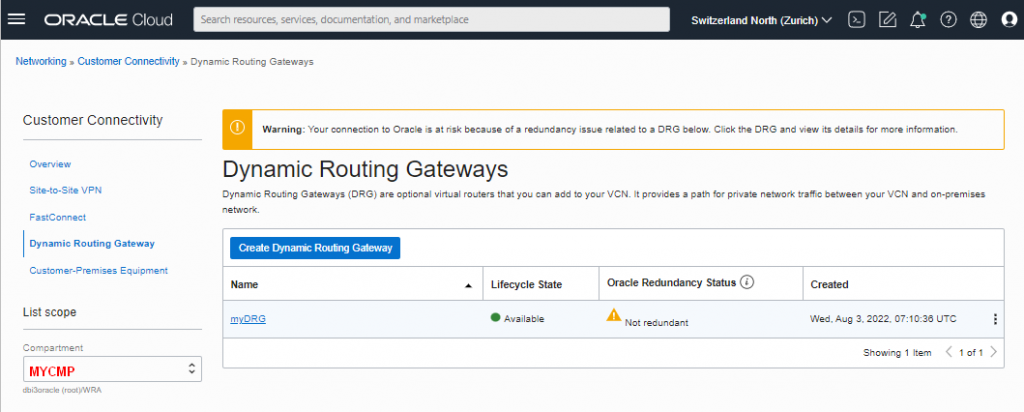
Shortly after setup I saw all ‘ok/status green’. But after some minutes one tunnel went down. Don’t worry, if the active tunnel has problems the other tunnel becomes active.
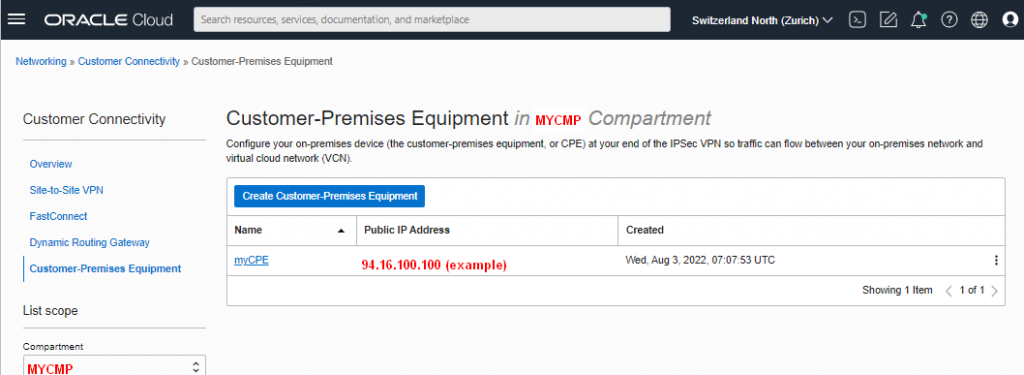
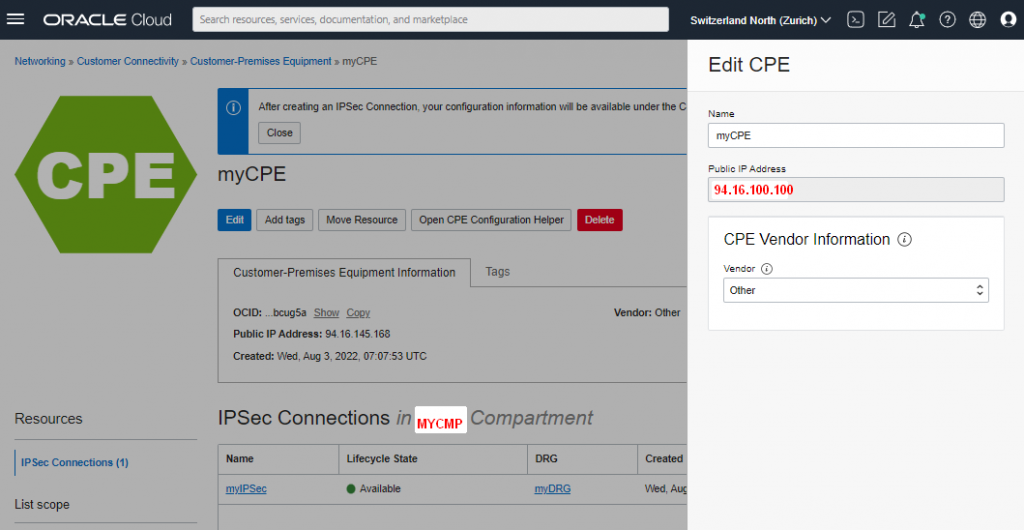
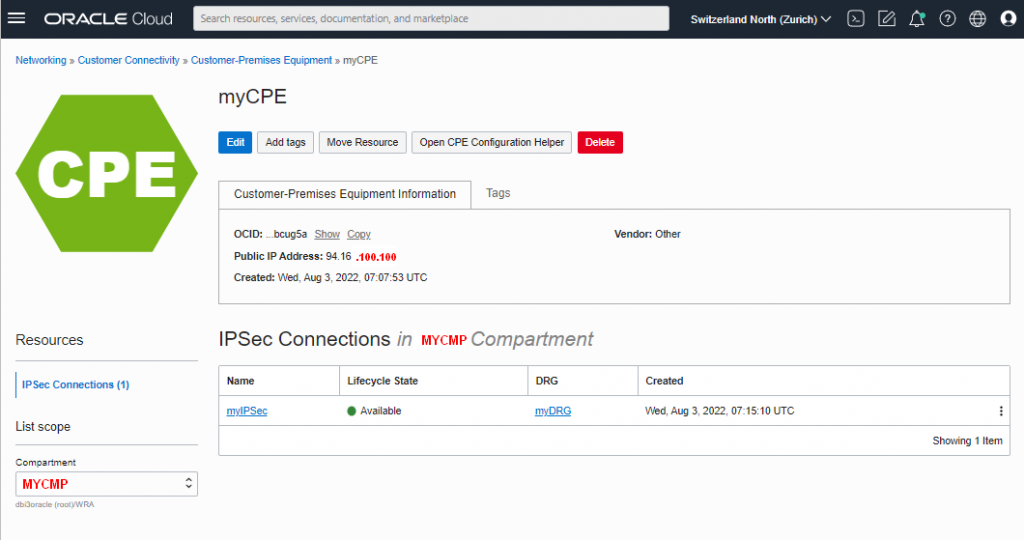
CPE
| Name | myCPE |
| Publ. IP | 94.16.100.100 (you must replace this with your public IP-address !!! ) |
Here you are able to use an IP-address only and that is the reason why you have to recreate it every day if you use your private dynamic IP-address.
In addition – the whole IPSec configuration depends on this. You have to recreate IPSec and the both tunnels too, even if you could use the same parameters with your own DNS/URL.
IPSec
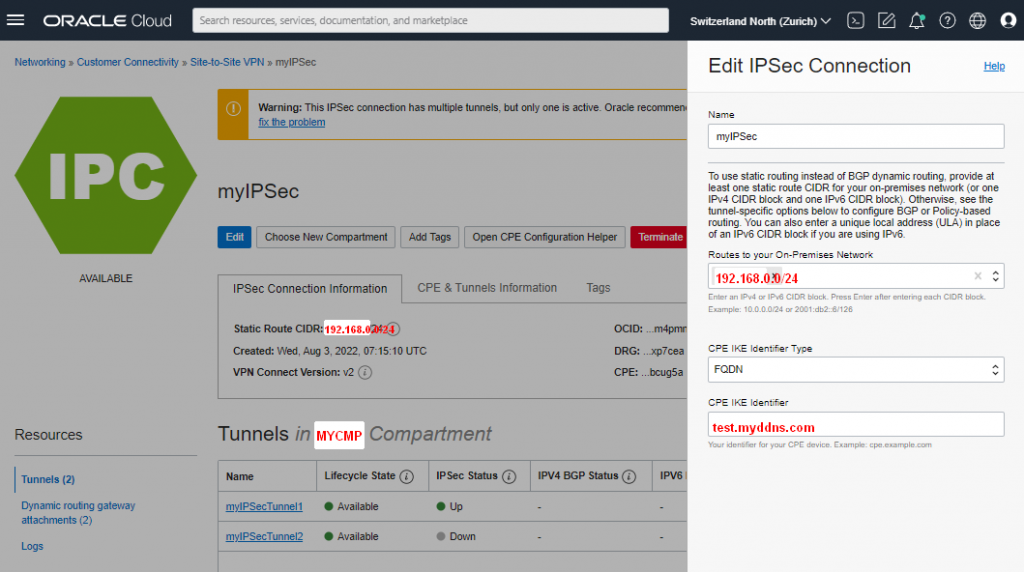
| Name | myIPSec |
| Lifecycle St. | Available |
| DRG | myDRG |
/!\ Here is the point you can change from IP-address to FQDN if you have your own DDNS or your own domain.
Tunnel
| Name | myIPSecTunnel1 |
| Lifecycle St | Available (when config successful) |
| IPSec Status | Up (when config successful) |
| IPv4 BGP St. | – |
| IPv6 BGP St. | – |
| Oracle VPN | 111.111.111.111 (address will be provided when created) |
| Routing Typ | Static Routing |
| Name | myIPSecTunnel2 |
| Lifecycle St | Available (when config successful) |
| IPSec Status | Up (when config successful) |
| IPv4 BGP St. | – |
| IPv6 BGP St. | – |
| Oracle VPN | 222.222.222.222 (address will be provided when created) |
| Routing Typ | Static Routing |
Here the pictures of OCI. I omitted the second tunnel as it is configured the same way.
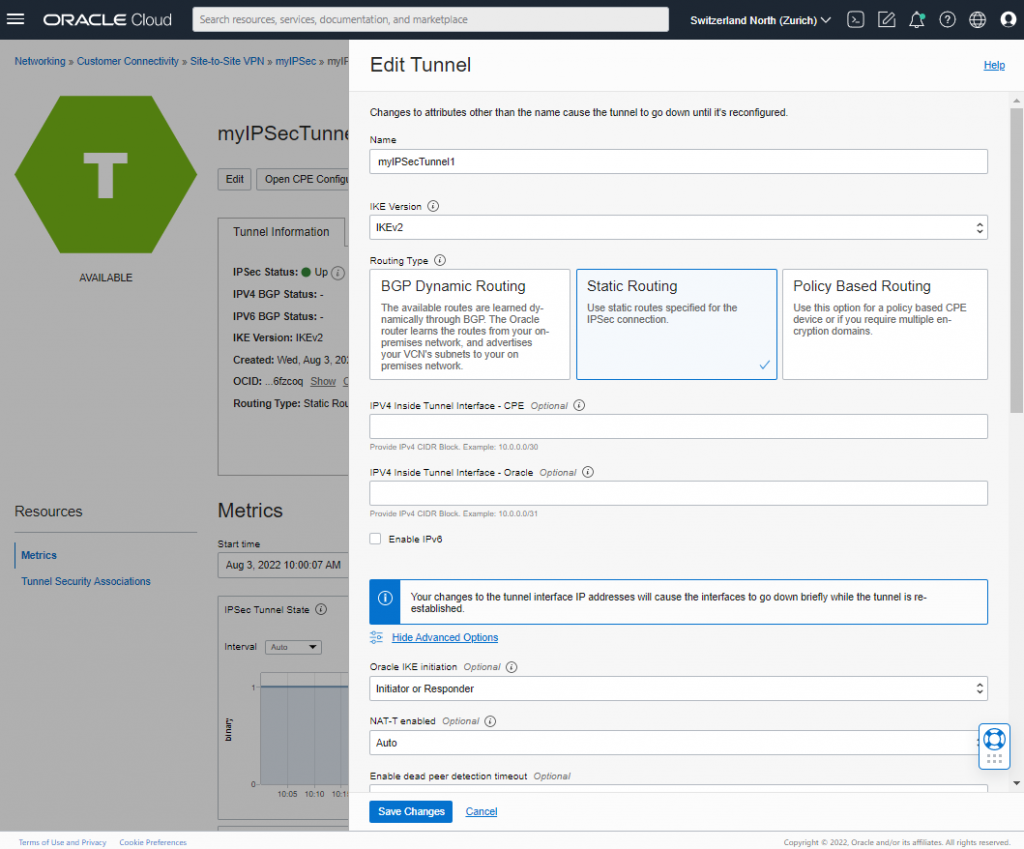
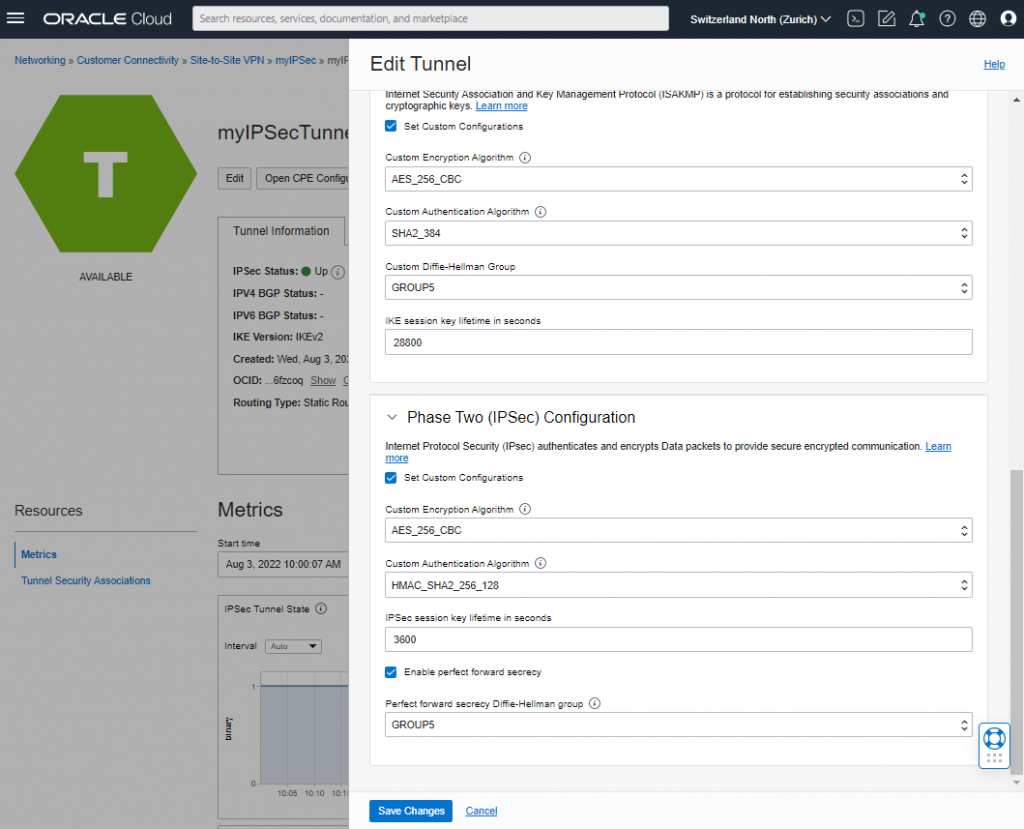
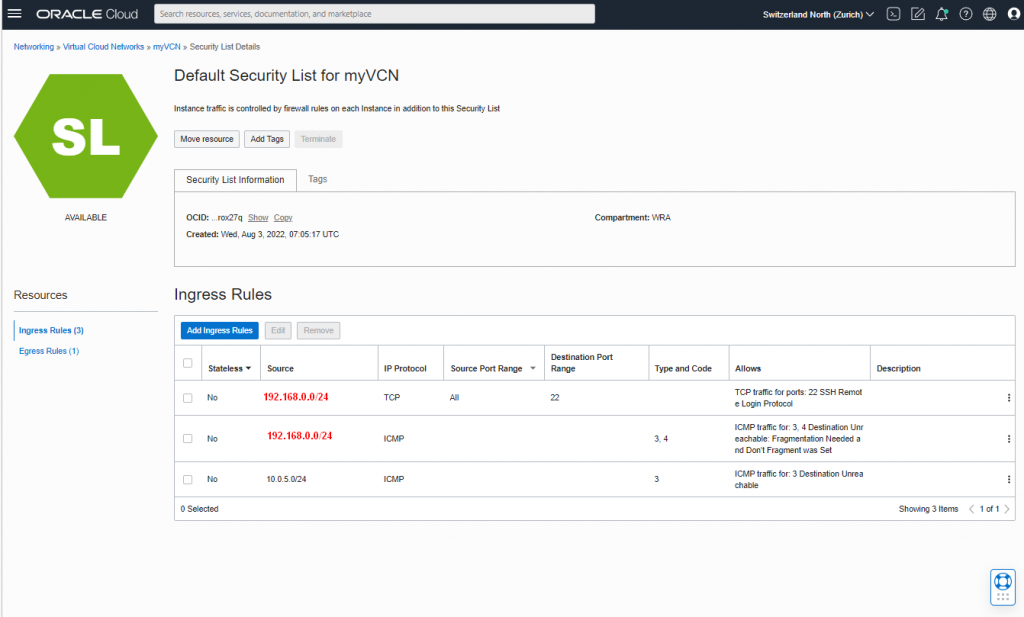
Security List (SL)
| SL | SecurityListMySubnet | |
| Ingress Rules (1) | ||
| Stateless | No | |
| Source | 192.168.0.0/24 [customers internal CIDR] | |
| IP Protocol | TCP | |
| Source PR | All | |
| Destin. PR | 22 | |
| Type&Code | ||
| Allows | TCP traffic for pots: 22 SSH Remote Login Protocol | |
| Description | myCPE(ingress) |
Please consider that I used (and copied) the default security list instead of creating the above mentioned ‘SecurityListMySubnet’
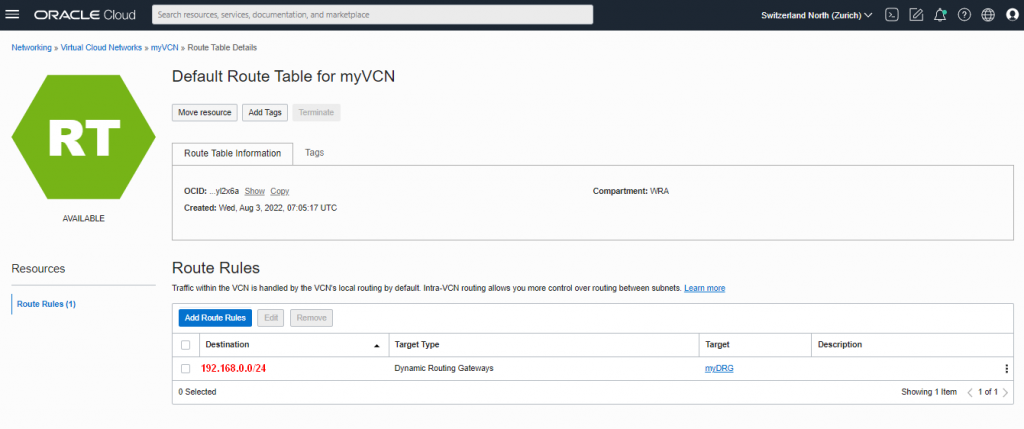
Routing Table (RT)
| RT | RouteTableMySubnet | |
| Destination | 192.168.0.0/24 [customers internal CIDR] | |
| Target Type | Dynamic Routing Gateway | |
| Target | myDRG |
Please consider that I used (and copied) the default route table instead of creating the above mentioned ‘RouteTableMySubnet’
Instance
Create an instance in your OCI VCN-subnet
Setup IPFire firewall
On the ‘Main page’ you will find your external IP if you connect your IPFire firewall directly to the internet. Otherwise you have to do the instructions provided by Oracle for NAT-configuration.
In this example it is the 94.16.100.100 IP-address which you have to replace with your external IP.
Main Page
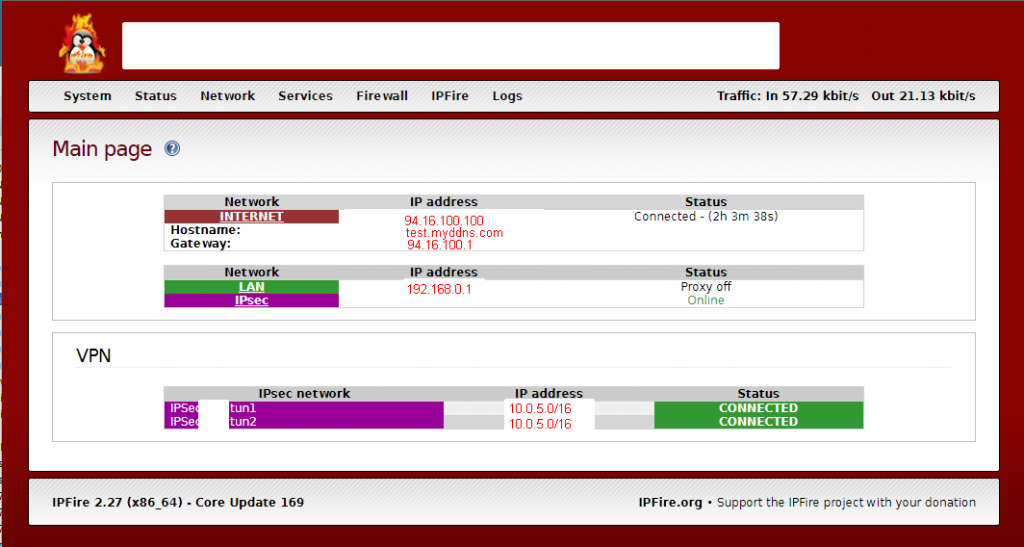
IPSec
Creating your Certificate Authorities and -Keys is self-explaining and I have filled my Host Certificate CN with my FQDN
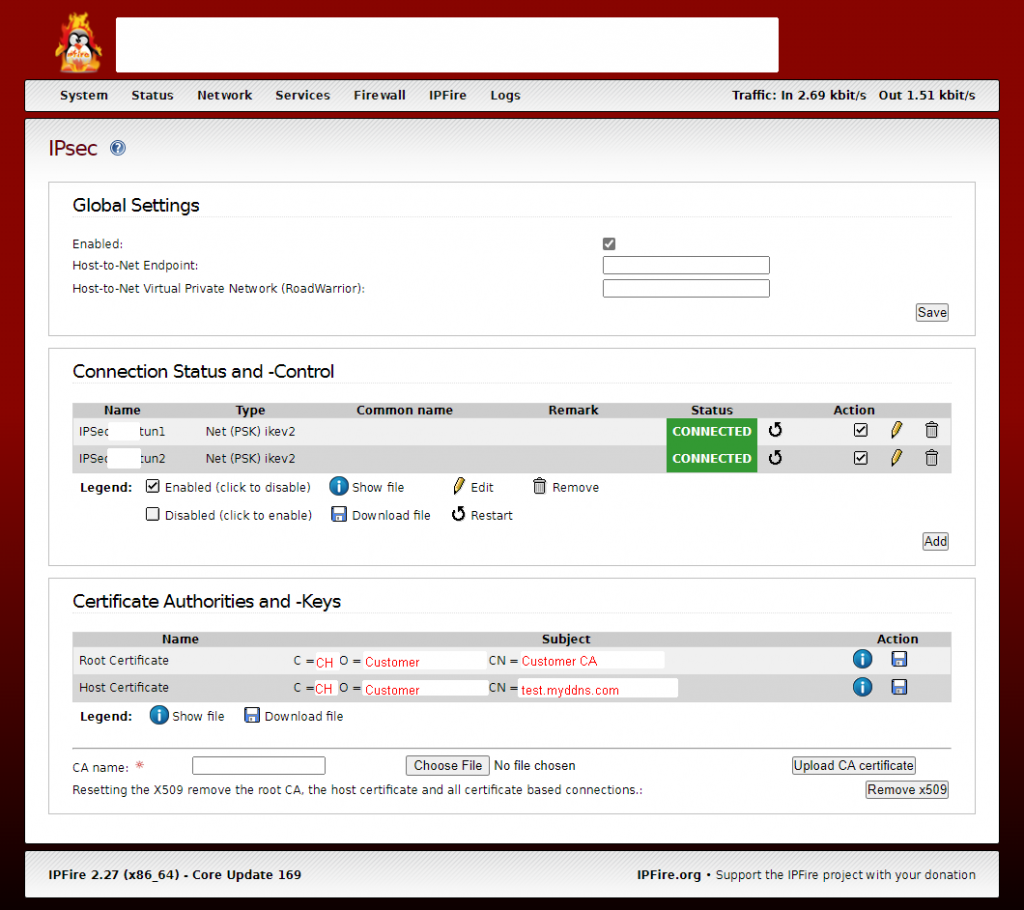
Don’t worry if one tunnel is displayed ‘down’ after some time. OCI and the firewall are automatically selecting one tunnel and take offline the other one if not configured with BGP.
Tunnel 1
Parameters for IPSec tunnel 1 on customer side is like this:
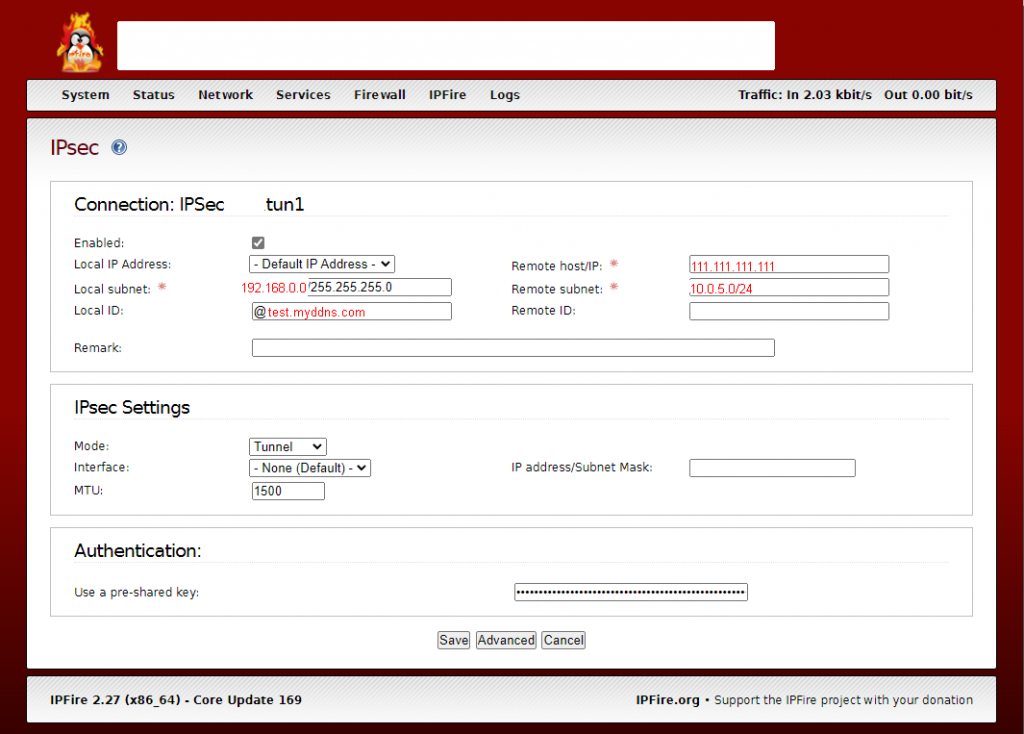
It is very important to fill ‘Local ID’ with ‘@<your FQDN>. You don’t get running tunnels in parallel if you don’t use the same naming as in OCI IPSec definition.
Tunnel 2
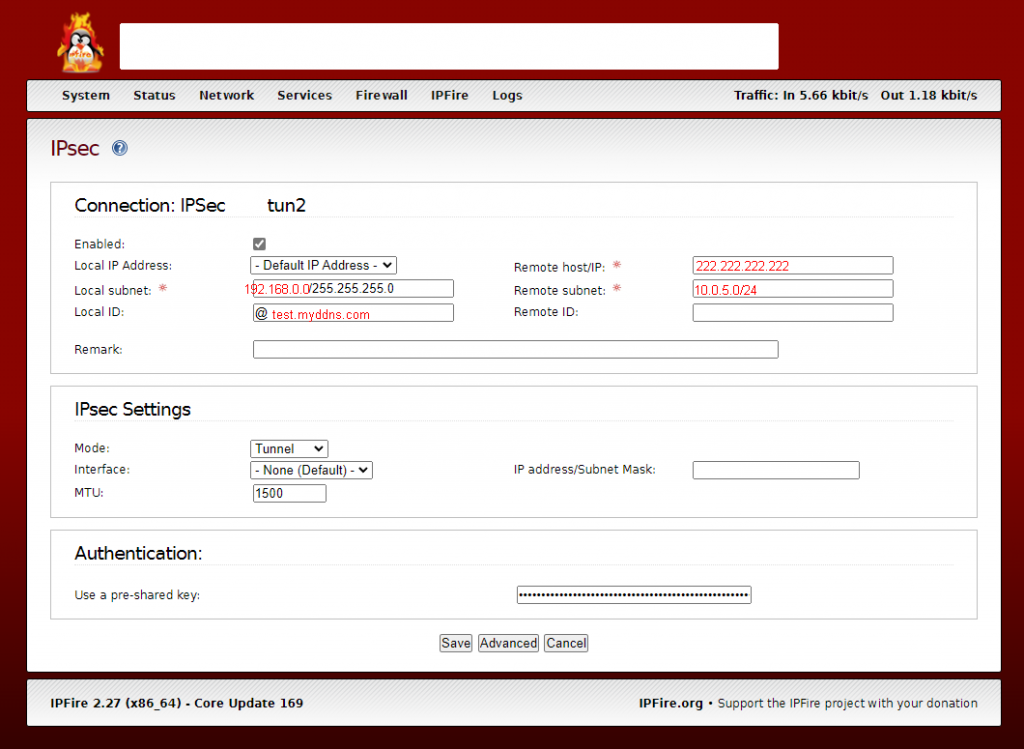
Same as tunnel 1: It is very important to fill ‘Local ID’ with ‘@<your FQDN>. You don’t get running tunnels in parallel if you don’t use the same naming as in OCI IPSec definition.
IPSec Tunnel Advanced
For IPSec advanced features I have set a custom configuration on OCI and my (customers) side. But it was running with defaults too. Advanced settings are identical for tunnel 1 and tunnel 2.
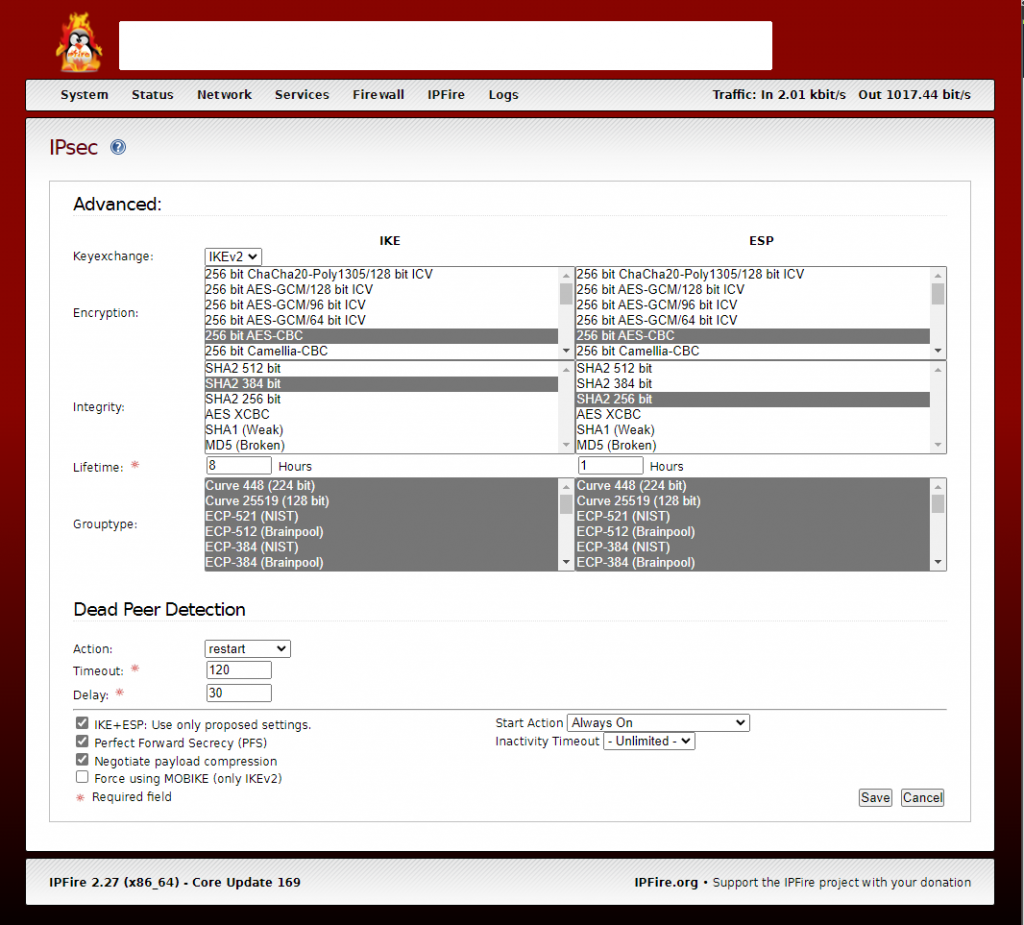
/!\ Don’t forget to set your IPFire firewall to allow traffic to both tunnels and drop traffic from tunnels if you don’t want that someone/something from OCI can access your private network.
By default the traffic is allowed in both directions.
Your personal firewall
Last but not least – don’t forget to block traffic from OCI to your personal network if you don’t want the ‘whole world’ in your personal network.
IPFire can handle the tunnels very easily. Just allow traffic from your network to tunnels and block (drop) traffic the way from tunnels to your network.
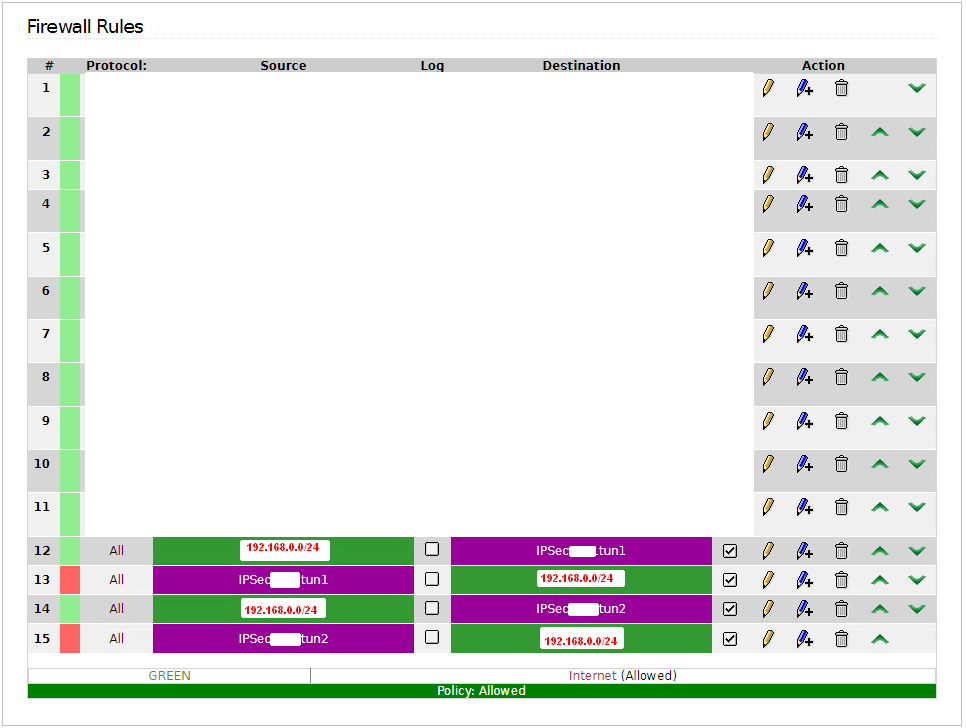
Faced issues
Most of the configuring was straight forward and the IPSec tunnels were showed up as working after a short time, but …
One single IPSec-tunnel ‘up’ works but the IPSec-tunnels don’t run in parallel
Most time-consuming issue was: Even if each IPSec tunnel was connected and ‘up’ to OCI, you don’t get any traffic through.
As a first try just disable one of the IPSec tunnels. My configuration worked with one tunnel up and the other down. And it doesn’t care which one I had up and which one was down. I just had to avoid using both in parallel.
What solved the issue?
The problem was gone when I used FQDN on OCI-side and entered the used FQDN in IPFire in the tunnel settings in the field ‘Local ID’ (with preceeded ‘@’ character)
What was the behavior then? With the FQDN in place OCI and my firewall were negotiating themselves which tunnel is used. One tunnel is up and one tunnel is down. If active tunnel goes down the other one goes up automatically.
Remark from Oracle:
If your CPE supports having two IPSec tunnels up/active to the same destination, configure the second tunnel to also be up/active. Oracle recommends configuring both tunnels to use BGP dynamic routing.
All other issues were mainly to ensure correct order of data-collecting and -entering. If you use OCIs ‘Wizard’ you are on safe side already.
Conclusion
For a ‘one day valid test’ (if you are using dynamic IP-address) it takes 3min reconfiguring of your environment every day after you’ve received a new external IP-address to do testing with OCI plus on premises IT with no financial impact. What you need is your curiosity and time setting things up initially.
![Thumbnail [60x60]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/WRA_web-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2024/01/HME_web.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/11/NIJ-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2024/04/SIT_web.png)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/JEW_web-min-scaled.jpg)
optimus
28.05.2023we have one on prem network connected to a vcn via ipsec and another vcn is connected to 1st vcn via drg, the problem is that onprem server has access to first vcn but cannot reach resources in second vcn, while there is reachability from 1st and 2nd vcn via drg but no communication direct from 2nd vcn to on prem subnet, looks like its routing only one subnet which is 1st vcn.
any possible solution ?
Wolfgang Rauchenstein
01.06.2023no communication is caused normally by missing or incomplete routing & acl. Check your Secutity List / Network Security Group settings too.
If you use the Network Visualizer in OCI you can see network information e.g. in the DRG when you click on a connection. Was helpful to me to 'see' it with triangles showing connection source-target direction