Here we are with Arnaud Berbier, up for our second conference day! You can check my blog for Day 1 if you’ve missed it.
Keynote sessions

Like yesterday, we started with a bunch of Keynote sessions from highly skilled speakers from the big Silicon Valley companies we all know about. It feels very much like an American show with lights effects and punchy music when the speaker arrives on stage. Big screens on each side of the enormous room show the presentation and the speakers. Yes, KubeCon / CloudNativeCon is a huge event!
If you visited the Kubernetes documentation website recently, you have seen the red banner at the top informing you that the container image registries of Kubernetes components have changed. I’ve learned today that it has been migrated to AWS! We then had announcements on CNCF projects that have been Graduated. Then some updates about CNCF projects. It is very quick but you can pick up new names in the CNCF landscape that I didn’t hear about before like dapr, Nydus or NATS.
I liked the way Guillaume Sauvage de Saint Marc presented OpenClarity on your application security. His compelling demonstration on security used a blurry picture. From it you can spot some bits and everything looks OK. However they are not enough to understand what is really going on when all that picture becomes clear. That is a great way to demonstrate how it is easy to miss the point in security (but not only!) if you don’t see clearly the full picture.
I’ve been amazed by the presentation of Emily Fox about saving knowledge through succession. The turnover of people and the increasing number of projects in the CNCF landscape put the risk of losing what has been learned. She compared this with a garden going through multiple seasons and what to do to take care of it and make it bloom. Each of her slide was very artistic and inspiring. The creativity and the combination of her slides and talk was just perfect. It is rare to be able to combine Art and IT and so it was remarkable. I very much appreciated it. Judge for yourself:

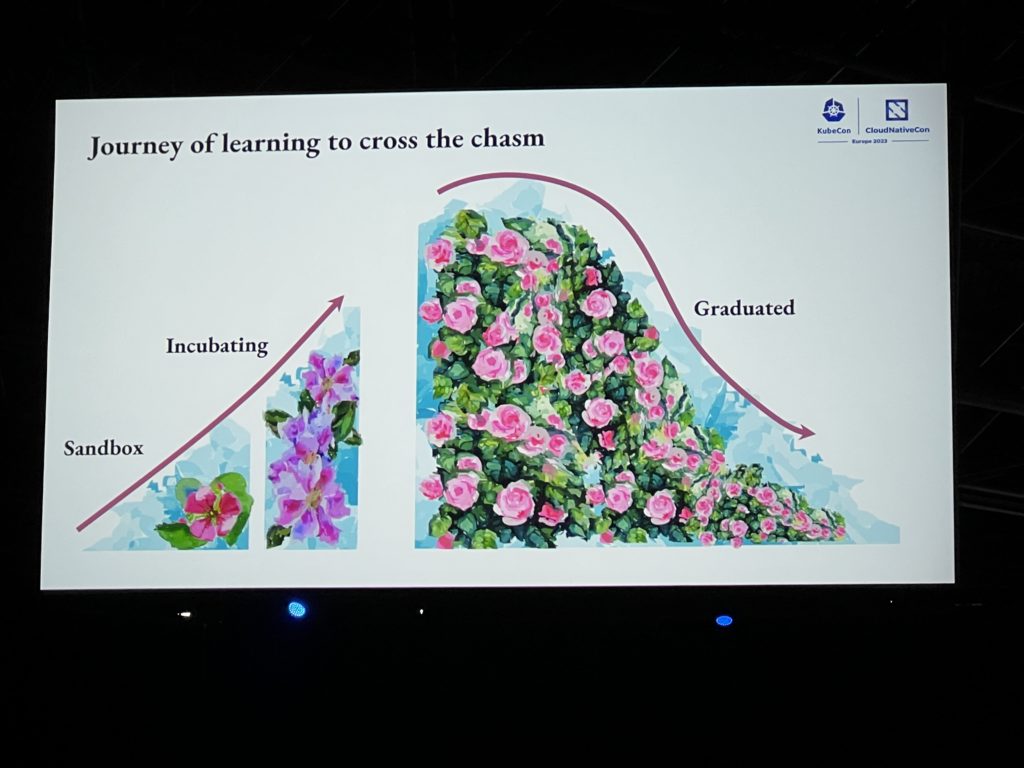

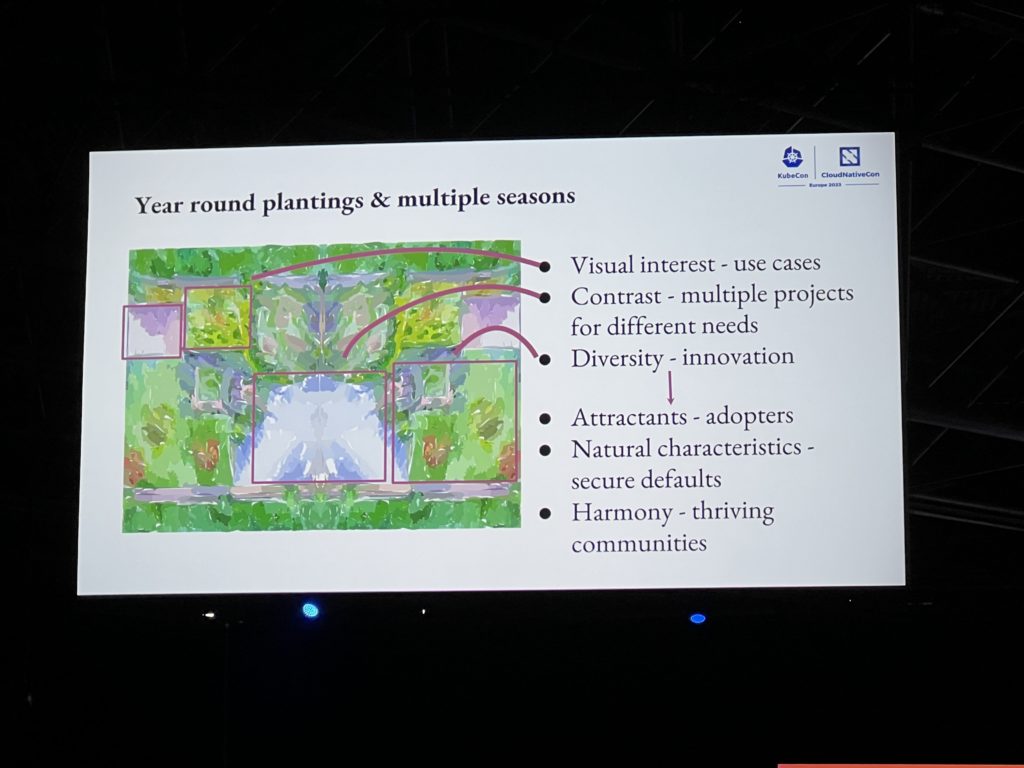
The security track
Yesterday I told you that I was interested in the Kubernetes Capture The Flag challenge that is happening today for 6 hours. There was so many interesting presentation today that I decided to attend them instead. However I keep that interest of mine in a part of my mind to catch another opportunity in the future. I’ve then continued to follow the security track as there were some attracting presentations that proved to be indeed amazing!
Matt Jarvis and Andrew Martin presented to us what the Next-Generation Cloud Native security could be. They warned us they don’t have a crystal ball and this is just hypothetical. Matt made fun of himself as he said in 1993 that “Internet will never take off”!
Kata containers should be there as well as anything that harden the isolation of the container. Another path for the future is improved hardware that will better protect the memory. Mainly the hardware architecture of computers remained the same since the beginning, only the size of the components have reduced. The Capability Hardware Enhanced RISC Instructions (CHERI) from the University of Cambridge tackles this topic. The kernel will evolve as well with eBPF and Rust. A lot of eBPF topics and discussions are around here and it is clearly a trend at the moment. Quantum computer are still a topic as well with the promise of between able to crack any current cryptography algorithm. So there is a need to find new algorithms that will resist them. Finally AI with the very popular ChatGPT showed a disruption in IT and will continue to be there. For security that means the finding of vulnerabilities can be automated with them. Remediation can also benefit from AI to automate the mitigation of cyberattacks.

The talk from Matt Turner and Francesco Beltramini about an automated Cloud Native response with Kubernetes and Service Mesh was very instructive. Look at this great drawing of “Kill Chain” which is just another name for the “Attack Path”:
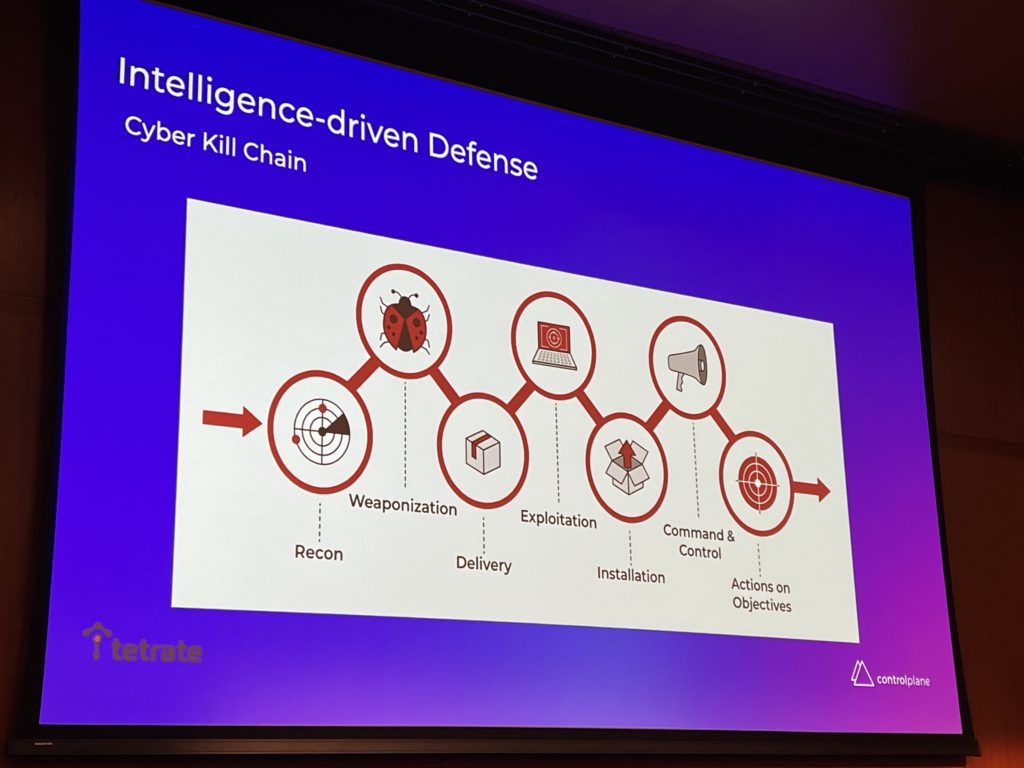
They showed the steps to do in the case an attack is detected in a Kubernetes cluster. Step by step they demonstrated how to isolate the Pod attacked, increase the verbosity of the logs and capturing all the information for doing forensics. From Kubernetes 1.25 you can use the kubectl debug command to debug a running Pod. I’ll need to try this!

They also showed how to use Envoy plugin Coraza to block malicious requests at layer 7.
Then I’ve missed a LIVE presentation of hacking and defending Kubernetes! The room was full 10 minutes before the start. Security is definitely a hot topic at the moment and this is pretty good news!
I could however save a seat to the session of Madhu Akula that ended up full as well. He is the creator of Goat which is an interactive security learning playground (I’ll definitely try this out!). He demonstrated LIVE at the speed of light several hacks in a Kubernetes cluster. Really cool!
The Kubernetes track
I’ve followed a presentation of Open Feature which is a Kubernetes based application for injecting flagD into workloads that wish to use Feature Flagging. FlagD is an application for reading a Feature Flag file and serving those flags back over an API. Typically we test cluster infrastructure and then we test code. FeatureFlagging lets you synchronise the conditions of application flow and infrastructure simultaneously. I’m totally unfamiliar with all of this but that is another interesting part of such conferences, it is to extend your knowledge.
For my last session of the day, I’ve selected a presentation about using volumes in Kubernetes across namespace boundaries. Up to now it is difficult to share data between namespace, for example between a Prod and a Dev namespace. From Kubernetes v1.26 there is now an alpha feature to provision volumes from cross-namespace data sources.
A movie to end the day
The movie “Inside Envoy” I talked about yesterday in my blog was broadcasted tonight. It is recorded like a Netflix documentary and is about the history of Envoy from the people involved in this adventure. Envoy is a layer 7 proxy with a lot of features and it was interesting to learn how it became what we have today.
It was an intense day as expected, tomorrow will be the last one. Stay tuned!
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2025/05/martin_bracher_2048x1536.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2024/03/AHI_web.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/HER_web-min-scaled.jpg)