After doing some more upgrades from Documentum 20.2 to 23.4, including D2, I faced a funny error about invalid licenses (DM_LICENSE_E_INVALID_LICENSE) while trying to login to D2 through OTDS SSO. That’s interesting because there is no license management for Documentum in 23.x, it only starts from 24.4 onwards. This is the (pretty) error in question:
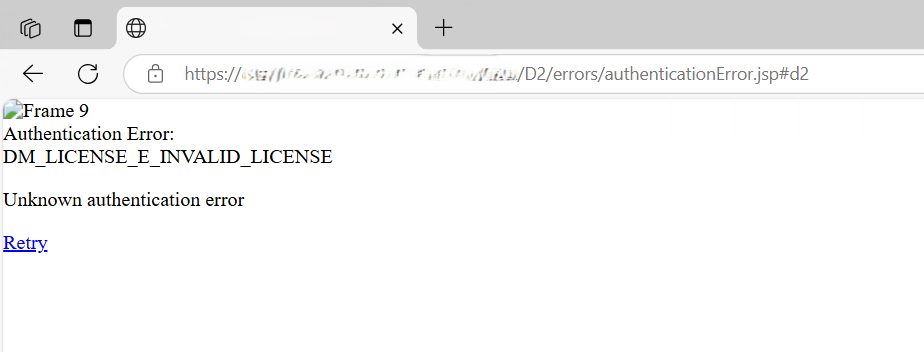
As a disclaimer, this customer is using D2 23.4 but with OTDS 24.4. I haven’t tried with an OTDS 23.4, so it is not impossible that the page might look different… For information, this error might be caused by multiple factors. The most common one is when you are already authenticated in OTDS (either through /otds-admin/ or even through another end-user Application like another D2 Repository) and trying to access a Repository for which you do not have an account. In this case you will get the message “DM_LICENSE_E_INVALID_LICENSE“. Trying to open another D2 will not change who you are currently logged in with, even if the SSO is enabled, and it will just re-use the current cookie (“http.cookie” being the higher priority Auth Handler in OTDS, for performance reasons).
At that time, the D2 logs was showing the following:
2025-10-08 13:22:28,435 UTC [INFO ] (https-jsse-nio-8080-exec-15) - c.emc.x3.portal.server.X3HttpSessionListener : Created http session ABE9F0D6D82E68FA9422A5B213455A4B
2025-10-08 13:22:28,435 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : No user name on the Http session yet
2025-10-08 13:22:28,436 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : No access_token found in Http request or Cookie Redirecting to OTDS Server
2025-10-08 13:22:28,436 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified scheme : https
2025-10-08 13:22:28,437 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified server name : d2.domain.com
2025-10-08 13:22:28,437 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified server port : 443
2025-10-08 13:22:28,438 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Built server host is : https://d2.domain.com:443
2025-10-08 13:22:28,438 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] header name=Host, value=d2.domain.com
2025-10-08 13:22:28,439 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] MaxHeaderValueSize: 8192
2025-10-08 13:22:28,439 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] validating the input valued2.domain.com
2025-10-08 13:22:28,440 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified host : d2.domain.com
2025-10-08 13:22:28,440 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Overall base URL built : https://d2.domain.com/D2
2025-10-08 13:22:28,441 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : Redirection url post encoding - https%3A%2F%2Fd2.domain.com%2FD2%2Fd2_otds.html%3ForigUrl%3D%2FD2%2F
2025-10-08 13:22:28,441 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : OAUTH final login sendRedirect URL : https://otds-mfa.domain.com/otdsws/oauth2/auth?response_type=token&client_id=dctm-ns-d2&redirect_uri=https%3A%2F%2Fd2.domain.com%2FD2%2Fd2_otds.html%3ForigUrl%3D%2FD2%2F&logon_appname=Documentum+Client+CE+23.4
2025-10-08 13:22:28,442 UTC [DEBUG] (https-jsse-nio-8080-exec-15) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : Sending redirection as it's not a rpc call : https://otds-mfa.domain.com/otdsws/oauth2/auth?response_type=token&client_id=dctm-ns-d2&redirect_uri=https%3A%2F%2Fd2.domain.com%2FD2%2Fd2_otds.html%3ForigUrl%3D%2FD2%2F&logon_appname=Documentum+Client+CE+23.4
2025-10-08 13:22:29,661 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] MaxHeaderKeySize: 256
2025-10-08 13:22:29,662 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] MaxHeaderValueSize: 8192
2025-10-08 13:22:29,663 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : No user name on the Http session yet
2025-10-08 13:22:29,663 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : Found access_token on Http Cookie, invalidating the cookie by setting maxAge 0
2025-10-08 13:22:29,663 UTC [INFO ] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : setting the cookie as secure as its a https request
2025-10-08 13:22:29,664 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : OTDS responded with a oauth token
2025-10-08 13:22:29,664 UTC [INFO ] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : ------ Begin getUntrustedJwtHeader : eyJraWQiOiJjZTU1...hilhGwaaPyHvrHQ
2025-10-08 13:22:29,665 UTC [INFO ] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : getUntrustedJwtHeader oauthTokenWithoutSignature : eyJraWQiOiJjZTU1...XNieGN0LWQyIn0.
2025-10-08 13:22:29,834 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : ------ Begin validateOTDSTokenClaims : MYUSERID
2025-10-08 13:22:29,834 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : validateOTDSTokenClaims for user : MYUSERID , OTDS : currenttime: 1759929749834 expirationtime: 1759933349000
2025-10-08 13:22:29,835 UTC [INFO ] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : ------ End validateOTDSTokenClaims : MYUSERID
2025-10-08 13:22:29,836 UTC [INFO ] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : PublicKey for Key id : ce55c...5acd9 exists
2025-10-08 13:22:29,837 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS Deafault Repository from shiro configured : REPO_NAME
2025-10-08 13:22:29,837 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : generating DM_Ticket for user : MYUSERID in Repository : REPO_NAME
2025-10-08 13:22:30,948 UTC [ERROR] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : OAuth Token Error occurred while generating a DCTM MultiUse Ticket for user : MYUSERID
2025-10-08 13:22:30,948 UTC [ERROR] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : OAuth Token Error please validate the OTDS Config of user exists in Repository
com.documentum.fc.client.DfAuthenticationException: [DM_SESSION_E_AUTH_FAIL]error: "Authentication failed for user myuserid with docbase REPO_NAME."
at com.documentum.fc.client.impl.docbase.DocbaseExceptionMapper.newException(DocbaseExceptionMapper.java:52)
at com.documentum.fc.client.impl.connection.docbase.MessageEntry.getException(MessageEntry.java:39)
at com.documentum.fc.client.impl.connection.docbase.DocbaseMessageManager.getException(DocbaseMessageManager.java:137)
at com.documentum.fc.client.impl.connection.docbase.netwise.NetwiseDocbaseRpcClient.checkForMessages(NetwiseDocbaseRpcClient.java:332)
at com.documentum.fc.client.impl.connection.docbase.netwise.NetwiseDocbaseRpcClient.applyForObject(NetwiseDocbaseRpcClient.java:680)
at com.documentum.fc.client.impl.connection.docbase.DocbaseConnection$8.evaluate(DocbaseConnection.java:1572)
at com.documentum.fc.client.impl.connection.docbase.DocbaseConnection.evaluateRpc(DocbaseConnection.java:1272)
at com.documentum.fc.client.impl.connection.docbase.DocbaseConnection.applyForObject(DocbaseConnection.java:1564)
at com.documentum.fc.client.impl.docbase.DocbaseApi.authenticateUser(DocbaseApi.java:1894)
at com.documentum.fc.client.impl.connection.docbase.DocbaseConnection.authenticate(DocbaseConnection.java:460)
at com.documentum.fc.client.impl.connection.docbase.DocbaseConnection.open(DocbaseConnection.java:140)
at com.documentum.fc.client.impl.connection.docbase.DocbaseConnection.<init>(DocbaseConnection.java:109)
at com.documentum.fc.client.impl.connection.docbase.DocbaseConnection.<init>(DocbaseConnection.java:69)
at com.documentum.fc.client.impl.connection.docbase.DocbaseConnectionFactory.newDocbaseConnection(DocbaseConnectionFactory.java:32)
at com.documentum.fc.client.impl.connection.docbase.DocbaseConnectionManager.createNewConnection(DocbaseConnectionManager.java:202)
at com.documentum.fc.client.impl.connection.docbase.DocbaseConnectionManager.getDocbaseConnection(DocbaseConnectionManager.java:132)
at com.documentum.fc.client.impl.session.SessionFactory.newSession(SessionFactory.java:24)
...
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:52)
at org.apache.tomcat.util.threads.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1190)
at org.apache.tomcat.util.threads.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:659)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:63)
at java.base/java.lang.Thread.run(Thread.java:840)
2025-10-08 13:22:30,949 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : redirectToErrorPage : Redirecting to Error Page as Login failed for user : null and exception : {}
com.emc.x3.portal.server.filters.authc.X3OTDSAuthenticationFilter$1: Authentication failed for user myuserid with repository REPO_NAME.
at com.emc.x3.portal.server.filters.authc.X3OTDSAuthenticationFilter.validateTokenAndGetUserId(X3OTDSAuthenticationFilter.java:1167)
at com.emc.x3.portal.server.filters.authc.X3OTDSAuthenticationFilter.onAccessDenied(X3OTDSAuthenticationFilter.java:293)
at org.apache.shiro.web.filter.AccessControlFilter.onAccessDenied(AccessControlFilter.java:133)
at org.apache.shiro.web.filter.AccessControlFilter.onPreHandle(AccessControlFilter.java:162)
at org.apache.shiro.web.filter.PathMatchingFilter.isFilterChainContinued(PathMatchingFilter.java:223)
at org.apache.shiro.web.filter.PathMatchingFilter.preHandle(PathMatchingFilter.java:198)
...
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:52)
at org.apache.tomcat.util.threads.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1190)
at org.apache.tomcat.util.threads.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:659)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:63)
at java.base/java.lang.Thread.run(Thread.java:840)
2025-10-08 13:22:30,950 UTC [INFO ] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : Adding the LicenseException to the Session : DM_SESSION_E_AUTH_FAIL
2025-10-08 13:22:30,950 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified scheme : https
2025-10-08 13:22:30,951 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified server name : d2.domain.com
2025-10-08 13:22:30,952 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified server port : 443
2025-10-08 13:22:30,952 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Built server host is : https://d2.domain.com:443
2025-10-08 13:22:30,953 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] header name=Host, value=d2.domain.com
2025-10-08 13:22:30,953 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] MaxHeaderValueSize: 8192
2025-10-08 13:22:30,953 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] validating the input valued2.domain.com
2025-10-08 13:22:30,954 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified host : d2.domain.com
2025-10-08 13:22:30,954 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Overall base URL built : https://d2.domain.com/D2
2025-10-08 13:22:30,954 UTC [DEBUG] (https-jsse-nio-8080-exec-25) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : D2 redirecting to errorPage JSP : https://d2.domain.com/D2/errors/authenticationError.jsp
2025-10-08 13:22:30,975 UTC [DEBUG] (https-jsse-nio-8080-exec-27) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] MaxHeaderKeySize: 256
2025-10-08 13:22:30,975 UTC [DEBUG] (https-jsse-nio-8080-exec-27) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] MaxHeaderValueSize: 8192
2025-10-08 13:22:30,976 UTC [DEBUG] (https-jsse-nio-8080-exec-27) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : No LicenseExcepton found on HttpSession hence not Redirectling to License ErrorPage
2025-10-08 13:22:30,976 UTC [DEBUG] (https-jsse-nio-8080-exec-27) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Selected Repository : REPO_NAME
2025-10-08 13:22:30,977 UTC [DEBUG] (https-jsse-nio-8080-exec-27) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] MaxHeaderKeySize: 256
2025-10-08 13:22:30,977 UTC [DEBUG] (https-jsse-nio-8080-exec-27) - o.o.e.logging.slf4j.Slf4JLogLevelHandlers$4 : [EVENT SUCCESS -> /D2/HTTPUtilities] MaxHeaderValueSize: 8192
2025-10-08 13:22:30,979 UTC [INFO ] (https-jsse-nio-8080-exec-27) - c.emc.x3.portal.server.X3HttpSessionListener : Expired Http session id : ABE9F0D6D82E68FA9422A5B213455A4B
2025-10-08 13:22:30,979 UTC [DEBUG] (https-jsse-nio-8080-exec-27) - com.emc.x3.server.context.ContextManager : Create a new context manager
As you can see above, it starts properly but when it contacts the Repository to try to generate a multi-use ticket, that’s where things go south. To try to understand what was going on, I started looking into my Repository account and I quickly saw that I actually had 2 accounts, one in lowercase (a legacy account) and a more recent one in uppercase:
[dmadmin@cs-0 log]$ iapi $DOCBASE_NAME -Udmadmin -Pxxx << EOC
> ?,c,select r_object_id, user_source, user_login_name, user_name from dm_user where lower(user_login_name)='myuserid';
> exit
> EOC
OpenText Documentum iapi - Interactive API interface
Copyright (c) 2023. OpenText Corporation
All rights reserved.
Client Library Release 23.4.0000.0180
Connecting to Server using docbase REPO_NAME
[DM_SESSION_I_SESSION_START]info: "Session 010123458029cff3 started for user dmadmin."
Connected to OpenText Documentum Server running Release 23.4.0000.0143 Linux64.Oracle
Session id is s0
API>
r_object_id user_source user_login_name user_name
---------------- ---------------- ------------------ ---------------------------
1101234580000d41 OTDS myuserid Patou Morgan (External)
1101234580ec1004 OTDS MYUSERID Patou Morgan
(2 rows affected)
API> Bye
[dmadmin@cs-0 log]$
There is quite a bit of background here but basically on older versions of Documentum, lowercase accounts were used at that customer with an old LDAP that isn’t around anymore and with the switch to OTDS and the new Azure EntraID, it became uppercase for simplicity. That switch from lowercase to uppercase was handled during the upgrade itself. However, my account was granted access to this Application only after the upgrade and as you can see above, the “user_name” and “user_login_name” differs. As a side note, OTDS will usually execute this kind of query to find existing users: “select * from dm_user where (user_name = ‘Patou Morgan’ or user_login_name = ‘MYUSERID’) and user_source = ‘OTDS’“.
Unfortunately, on my very old account, the user_name was slightly different and therefore OTDS didn’t understand that I already had an account, and it just created a new one, in UPPERCASE, instead of updating the old one. That’s also the reason why I highly suggested that customer to change all lowercase to uppercase user_login_name post migration, so that it would allow the OTDS to correctly map users and avoid creating duplicate accounts, but that’s another topic.
I suspected this duplicate to be the root cause of the issue, and enabling the authentication trace on the Repository definitively confirmed it:
2025-10-08T13:22:30.541999 3057168[3057168] 010123458029d042 [AUTH] Entering RPC AUTHENTICATE_USER
2025-10-08T13:22:30.542064 3057168[3057168] 010123458029d042 [AUTH] Start Authentication : LOGON_NAME=MYUSERID, DOMAIN_NAME=, OS_LOGON_NAME=tomcat, OS_LOGON_DOMAIN=, ASSUME_USER=0, TRUSTED_LOGIN_ALLOWED=1, PRINCIPAL_AUTH=0, DO_SET_LOCALE=0, RECONNECT=0, CLIENT_TOKEN=[82, -30, -86, 7, -113, -35, 124, 3, 106, -45, -4, -117, -117, 39, 109]
2025-10-08T13:22:30.542076 3057168[3057168] 010123458029d042 [AUTH] Start Authenticate Client Instance
2025-10-08T13:22:30.542103 3057168[3057168] 010123458029d042 [AUTH] Start Verify Signature, Client : dfc_H4qo73YaRaBAOd9sGtc7pKJlWkwa , Host : d2-0.d2.dctm-ns.svc.cluster.local
2025-10-08T13:22:30.550074 3057168[3057168] 010123458029d042 [AUTH] End Verify Signature, Client : dfc_H4qo73YaRaBAOd9sGtc7pKJlWkwa , Host : d2-0.d2.dctm-ns.svc.cluster.local
2025-10-08T13:22:30.550128 3057168[3057168] 010123458029d042 [AUTH] End Authenticate Client Instance
2025-10-08T13:22:30.575328 3057168[3057168] 010123458029d042 [AUTH] Start-AuthenticateUser: ClientHost(d2-0.d2.dctm-ns.svc.cluster.local), LogonName(MYUSERID), LogonOSName(tomcat), LogonOSDomain(), UserExtraDomain(), ServerDomain()
2025-10-08T13:22:30.575389 3057168[3057168] 010123458029d042 [AUTH] Start-AuthenticateUserName:
2025-10-08T13:22:30.575404 3057168[3057168] 010123458029d042 [AUTH] dmResolveNamesForCredentials: auth_protocol()
2025-10-08T13:22:30.577804 3057168[3057168] 010123458029d042 [AUTH] [DM_SESSION_E_USER_LOGIN_NAME_CONFLICT]error: "Userloginname myuserid conflict with another user"
2025-10-08T13:22:30.577838 3057168[3057168] 010123458029d042 [AUTH] [DM_USER_E_NOT_DOCUMENTUM_USER]error: "User myuserid does not exist in the docbase"
2025-10-08T13:22:30.577851 3057168[3057168] 010123458029d042 [AUTH] End-AuthenticateUserName: dm_user.user_login_domain(), Result: 0
2025-10-08T13:22:30.577862 3057168[3057168] 010123458029d042 [AUTH] Not Found dm_user.user_login_name(myuserid), dm_user.user_login_domain()
2025-10-08T13:22:30.945436 3057168[3057168] 010123458029d042 [AUTH] Final Auth Result=F, LOGON_NAME=myuserid, AUTHENTICATION_LEVEL=1, OS_LOGON_NAME=tomcat, OS_LOGON_DOMAIN=, CLIENT_HOST_NAME=d2-0.d2.dctm-ns.svc.cluster.local, CLIENT_HOST_ADDR=172.1.1.1, USER_LOGON_NAME_RESOLVED=1, AUTHENTICATION_ONLY=0, USER_NAME=, USER_OS_NAME=myuserid, USER_LOGIN_NAME=myuserid, USER_LOGIN_DOMAIN=, USER_EXTRA_CREDENTIAL[0]=, USER_EXTRA_CREDENTIAL[1]=, USER_EXTRA_CREDENTIAL[2]=e2, USER_EXTRA_CREDENTIAL[3]=, USER_EXTRA_CREDENTIAL[4]=, USER_EXTRA_CREDENTIAL[5]=, SERVER_SESSION_ID=010123458029d042, AUTH_BEGIN_TIME=Wed Oct 8 13:22:30 2025, AUTH_END_TIME=Wed Oct 8 13:22:30 2025, Total elapsed time=0 seconds
2025-10-08T13:22:30.945484 3057168[3057168] 010123458029d042 [AUTH] Exiting RPC AUTHENTICATE_USER
My next step was therefore to merge the 2 accounts, to see if the SSO was working again. I could use the Re-Assign action on Documentum Administrator to do that, but for this blog, I wanted to do it through command line. Therefore, I started with the creation of a new “dm_job_request” whose purpose is to reassign the lowercase account to the UPPERCASE one (note: I used iapi format here to show each key/value, but it might be easier and will be shorter / more compact through DQL):
[dmadmin@cs-0 log]$ iapi $DOCBASE_NAME -Udmadmin -Pxxx << EOC
> create,c,dm_job_request
> set,c,l,object_name
> UserRename
> set,c,l,job_name
> dm_UserRename
> set,c,l,method_name
> dm_UserRename
> set,c,l,request_completed
> F
> set,c,l,priority
> 0
> append,c,l,arguments_keys
> OldUserName
> append,c,l,arguments_values
> Patou Morgan (External)
> append,c,l,arguments_keys
> NewUserName
> append,c,l,arguments_values
> Patou Morgan
> append,c,l,arguments_keys
> report_only
> append,c,l,arguments_values
> F
> append,c,l,arguments_keys
> unlock_locked_obj
> append,c,l,arguments_values
> T
> link,c,l,/System/Sysadmin/UserRename
> save,c,l
> exit
> EOC
OpenText Documentum iapi - Interactive API interface
Copyright (c) 2023. OpenText Corporation
All rights reserved.
Client Library Release 23.4.0000.0180
Connecting to Server using docbase REPO_NAME
[DM_SESSION_I_SESSION_START]info: "Session 010123458029d04d started for user dmadmin."
Connected to OpenText Documentum Server running Release 23.4.0000.0143 Linux64.Oracle
Session id is s0
API> ...
08012345800c1797
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> SET> ...
OK
API> ...
OK
API> ...
OK
API> Bye
[dmadmin@cs-0 log]$
Then you would need to execute/run the “dm_UserRename” job, so it can process the requests. This can also be done through DA (note: the Re-Assign on DA can also trigger the job directly too) but let’s continue with the command line option:
[dmadmin@cs-0 log]$ iapi $DOCBASE_NAME -Udmadmin -Pxxx << EOC
> ?,c,update dm_job objects set run_now=true, set a_next_invocation=date(now) where object_name='dm_UserRename';
> exit
> EOC
OpenText Documentum iapi - Interactive API interface
Copyright (c) 2023. OpenText Corporation
All rights reserved.
Client Library Release 23.4.0000.0180
Connecting to Server using docbase REPO_NAME
[DM_SESSION_I_SESSION_START]info: "Session 010123458029d05c started for user dmadmin."
Connected to OpenText Documentum Server running Release 23.4.0000.0143 Linux64.Oracle
Session id is s0
API>
objects_updated
---------------
1
(1 row affected)
[DM_QUERY_I_NUM_UPDATE]info: "1 objects were affected by your UPDATE statement."
API> Bye
[dmadmin@cs-0 log]$
Once the job ran, I was left with a single (correct) account:
[dmadmin@cs-0 log]$ iapi $DOCBASE_NAME -Udmadmin -Pxxx << EOC
> ?,c,select r_object_id, user_source, user_login_name, user_name from dm_user where lower(user_login_name)='myuserid';
> exit
> EOC
OpenText Documentum iapi - Interactive API interface
Copyright (c) 2023. OpenText Corporation
All rights reserved.
Client Library Release 23.4.0000.0180
Connecting to Server using docbase REPO_NAME
[DM_SESSION_I_SESSION_START]info: "Session 010123458029d063 started for user dmadmin."
Connected to OpenText Documentum Server running Release 23.4.0000.0143 Linux64.Oracle
Session id is s0
API>
r_object_id user_source user_login_name user_name
---------------- ---------------- ------------------ ---------------------------
1101234580ec1004 OTDS MYUSERID Patou Morgan
(1 row affected)
API> Bye
[dmadmin@cs-0 log]$
Without surprises, the SSO was working afterwards, as D2 could proceed with the multi-use ticket generation:
2025-10-08 13:37:45,779 UTC [INFO ] (https-jsse-nio-8080-exec-17) - c.emc.x3.portal.server.X3HttpSessionListener : Created http session AA7FD4CC34B6FE6779071D21E6B366CD
2025-10-08 13:37:45,780 UTC [DEBUG] (https-jsse-nio-8080-exec-17) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : No user name on the Http session yet
2025-10-08 13:37:45,780 UTC [DEBUG] (https-jsse-nio-8080-exec-17) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : No access_token found in Http request or Cookie Redirecting to OTDS Server
2025-10-08 13:37:45,781 UTC [DEBUG] (https-jsse-nio-8080-exec-17) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified scheme : https
2025-10-08 13:37:45,781 UTC [DEBUG] (https-jsse-nio-8080-exec-17) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified server name : d2.domain.com
2025-10-08 13:37:45,782 UTC [DEBUG] (https-jsse-nio-8080-exec-17) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Identified server port : 443
2025-10-08 13:37:45,782 UTC [DEBUG] (https-jsse-nio-8080-exec-17) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Built server host is : https://d2.domain.com:443
...
2025-10-08 13:37:45,946 UTC [DEBUG] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : No user name on the Http session yet
2025-10-08 13:37:45,946 UTC [DEBUG] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : Found access_token on Http Cookie, invalidating the cookie by setting maxAge 0
2025-10-08 13:37:45,946 UTC [INFO ] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : setting the cookie as secure as its a https request
2025-10-08 13:37:45,947 UTC [DEBUG] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : OTDS responded with a oauth token
2025-10-08 13:37:45,947 UTC [INFO ] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : ------ Begin getUntrustedJwtHeader : eyJraWQiOiJjZ...9pQDTqTmfRQ
2025-10-08 13:37:45,947 UTC [INFO ] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : getUntrustedJwtHeader oauthTokenWithoutSignature : eyJraWQiOiJjZ...eGN0LWQyIn0.
2025-10-08 13:37:46,134 UTC [DEBUG] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : ------ Begin validateOTDSTokenClaims : MYUSERID
2025-10-08 13:37:46,135 UTC [DEBUG] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : validateOTDSTokenClaims for user : MYUSERID , OTDS : currenttime: 1759930666135 expirationtime: 1759934265000
2025-10-08 13:37:46,136 UTC [INFO ] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : ------ End validateOTDSTokenClaims : MYUSERID
2025-10-08 13:37:46,136 UTC [INFO ] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : PublicKey for Key id : ce55c...5acd9 exists
2025-10-08 13:37:46,138 UTC [DEBUG] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS Deafault Repository from shiro configured : REPO_NAME
2025-10-08 13:37:46,138 UTC [DEBUG] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : generating DM_Ticket for user : MYUSERID in Repository : REPO_NAME
2025-10-08 13:37:47,289 UTC [INFO ] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : generateDCTMTicket : dm_ticket ticketTimeout generated for user : MYUSERID is 480 minutes
2025-10-08 13:37:47,295 UTC [DEBUG] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : DCTM MultiUseTicket generated for user : MYUSERID in repository : REPO_NAME
2025-10-08 13:37:47,295 UTC [DEBUG] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.authc.X3OTDSAuthenticationFilter : OTDS : OAUTH Token is validated and multiuse dctmticket generated for user : MYUSERID
2025-10-08 13:37:47,295 UTC [DEBUG] (https-jsse-nio-8080-exec-32) - c.e.x.p.s.f.a.X3TrustHttpAuthenticationFilter : Selected Repository : REPO_NAME
...
The Repository authentication trace was also showing a correct behavior (otherwise D2 wouldn’t have gotten the ticket):
2025-10-08T13:37:46.853755 3073303[3073303] 010123458029d067 [AUTH] Entering RPC AUTHENTICATE_USER
2025-10-08T13:37:46.853812 3073303[3073303] 010123458029d067 [AUTH] Start Authentication : LOGON_NAME=MYUSERID, DOMAIN_NAME=, OS_LOGON_NAME=tomcat, OS_LOGON_DOMAIN=, ASSUME_USER=0, TRUSTED_LOGIN_ALLOWED=1, PRINCIPAL_AUTH=0, DO_SET_LOCALE=0, RECONNECT=0, CLIENT_TOKEN=[82, -30, -86, 7, -113, -35, 124, 3, 106, -45, -4, -117, -117, 39, 109]
2025-10-08T13:37:46.853823 3073303[3073303] 010123458029d067 [AUTH] Start Authenticate Client Instance
2025-10-08T13:37:46.853858 3073303[3073303] 010123458029d067 [AUTH] Start Verify Signature, Client : dfc_H4qo73YaRaBAOd9sGtc7pKJlWkwa , Host : d2-0.d2.dctm-ns.svc.cluster.local
2025-10-08T13:37:46.862406 3073303[3073303] 010123458029d067 [AUTH] End Verify Signature, Client : dfc_H4qo73YaRaBAOd9sGtc7pKJlWkwa , Host : d2-0.d2.dctm-ns.svc.cluster.local
2025-10-08T13:37:46.862454 3073303[3073303] 010123458029d067 [AUTH] End Authenticate Client Instance
2025-10-08T13:37:46.888013 3073303[3073303] 010123458029d067 [AUTH] Start-AuthenticateUser: ClientHost(d2-0.d2.dctm-ns.svc.cluster.local), LogonName(MYUSERID), LogonOSName(tomcat), LogonOSDomain(), UserExtraDomain(), ServerDomain()
2025-10-08T13:37:46.888050 3073303[3073303] 010123458029d067 [AUTH] Start-AuthenticateUserName:
2025-10-08T13:37:46.888061 3073303[3073303] 010123458029d067 [AUTH] dmResolveNamesForCredentials: auth_protocol()
2025-10-08T13:37:46.891487 3073303[3073303] 010123458029d067 [AUTH] End-AuthenticateUserName: dm_user.user_login_domain(), Result: 1
2025-10-08T13:37:46.891511 3073303[3073303] 010123458029d067 [AUTH] Found dm_user.user_login_name(MYUSERID), dm_user.user_login_domain()
2025-10-08T13:37:46.891524 3073303[3073303] 010123458029d067 [AUTH] Start-AuthenticateDomain:LogonName(MYUSERID), UserExtraDomain(), auth_protocol()
2025-10-08T13:37:46.891539 3073303[3073303] 010123458029d067 [AUTH] AuthenticateDomain - no domain required:domainOverride(False), user_login_domain(), serverAuthTarget(), userAuthTarget()
2025-10-08T13:37:46.891548 3073303[3073303] 010123458029d067 [AUTH] End-AuthenticateDomain: 1
2025-10-08T13:37:46.891557 3073303[3073303] 010123458029d067 [AUTH] Start-AuthenticateUserState:UserLoginName(MYUSERID), UserExtraDomain()
2025-10-08T13:37:46.891571 3073303[3073303] 010123458029d067 [AUTH] Start-AuthenticateUserState:
2025-10-08T13:37:46.891581 3073303[3073303] 010123458029d067 [AUTH] dmStateForUser: auth_protocol()
2025-10-08T13:37:46.891594 3073303[3073303] 010123458029d067 [AUTH] End-AuthenticateUserState: 1
2025-10-08T13:37:46.891625 3073303[3073303] 010123458029d067 [AUTH] Start-AuthenticateByTrust:OSLogonName(tomcat), UserLoginName(MYUSERID), OSLogonDomain(), UserExtraDomain()
2025-10-08T13:37:46.892885 3073303[3073303] 010123458029d067 [AUTH] Trusted authentication failed because OS logon user name mis-match
2025-10-08T13:37:46.892912 3073303[3073303] 010123458029d067 [AUTH] End-AuthenticateByTrust: 0
2025-10-08T13:37:46.898219 3073303[3073303] 010123458029d067 [AUTH] Create Session Log for user : MYUSERID, FILE NAME : 010123458029d067
2025-10-08T13:37:46.908056 3073303[3073303] 010123458029d067 [AUTH] Done creating Session Log File for user : MYUSERID
2025-10-08T13:37:47.287354 3073303[3073303] 010123458029d067 [AUTH] Cannot find method dm_checkoutLicense.
2025-10-08T13:37:47.287656 3073303[3073303] 010123458029d067 [AUTH] Final Auth Result=T, LOGON_NAME=MYUSERID, AUTHENTICATION_LEVEL=10, OS_LOGON_NAME=tomcat, OS_LOGON_DOMAIN=, CLIENT_HOST_NAME=d2-0.d2.dctm-ns.svc.cluster.local, CLIENT_HOST_ADDR=172.1.1.1, USER_LOGON_NAME_RESOLVED=1, AUTHENTICATION_ONLY=0, USER_NAME=Patou Morgan, USER_OS_NAME=MYUSERID, USER_LOGIN_NAME=MYUSERID, USER_LOGIN_DOMAIN=, USER_EXTRA_CREDENTIAL[0]=, USER_EXTRA_CREDENTIAL[1]=, USER_EXTRA_CREDENTIAL[2]=e2, USER_EXTRA_CREDENTIAL[3]=, USER_EXTRA_CREDENTIAL[4]=, USER_EXTRA_CREDENTIAL[5]=, SERVER_SESSION_ID=010123458029d067, AUTH_BEGIN_TIME=Wed Oct 8 13:37:46 2025, AUTH_END_TIME=Wed Oct 8 13:37:47 2025, Total elapsed time=1 seconds
2025-10-08T13:37:47.287668 3073303[3073303] 010123458029d067 [AUTH] Exiting RPC AUTHENTICATE_USER
It is pretty obvious that duplicate accounts and other similar misconfigurations at the Repository level would cause issues with the login process, but what isn’t usual is getting an error related to invalid licenses for that, especially so since my account did exist in the Repository, Documentum was just not using the one that OTDS/D2 mentioned.
![Thumbnail [60x60]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/MOP_web-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/GME_web-min-scaled.jpg)