Before we explore Microsoft Defender & Arc, I must clarify:
Setting up Microsoft Defender and Arc on a Linux server, especially one without internet access and with robust security monitoring and hardening, may seem counterintuitive. However, because the software was already purchased, managers insist on deploying the same product across all servers. So here we are, deploying a Microsoft closed source antivirus on a Linux open source operating system. But don’t get me wrong, Defender and Arc do have some benefits which make it worth installing, you can find those in the Summary below.
The whole setup was done based on the Microsoft official best practice:
https://learn.microsoft.com/en-us/defender-endpoint/linux-install-manually
First, for all Distributions we will need the On-boarding script generated out of your companies Microsoft Azure environment. For that we need to go into the Microsoft Defender Portal:
- Head to Settings > Endpoints > Device Management > Onboarding.
- Next, in the first drop down, pick “Linux Server” as the operating system. In the second drop down, choose “Local Script” as the deployment method.
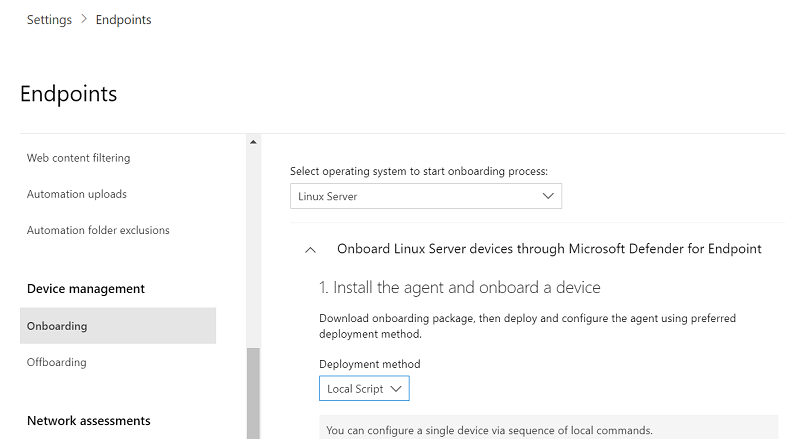
- After that, click “Download onboarding package” and save the file as WindowsDefenderATPOnboardingPackage.zip
Finally, unzip that file and drop it in the home directory of each server you want to join.
Preparing Microsoft Defender/ Arc for RPM-Based Distributions
# Jump to your home folder
$ cd
# Download the official azure installation script for defender
$ curl -o mde_install.sh https://github.com/microsoft/mdatp-xplat/blob/master/linux/installation/mde_installer.sh
# In case your Linux server has no direct internet access you can use curl with a Proxy. Use -x:
curl -x http://proxy.yourdomain.ch:80 -o mde_install.sh https://github.com/microsoft/mdatp-xplat/blob/master/linux/installation/mde_installer.sh
# Install dependencies which will be needed for the process
$ sudo yum install yum-utils
# Add the official repository for the defender and arc packages
$ sudo yum-config-manager --add-repo=https://packages.microsoft.com/config/rhel/8/prod.repo
# Trust the repositories by importing the GPG-Key
$ sudo rpm --import https://packages.microsoft.com/keys/microsoft.asc
# Install both packages
$ sudo apt-get install mdatp azcmagent
# Add a proxy to both the mdatp (Defender) and azcmagent (ARC)
$ sudo mdatp config proxy set --value http://proxy.yourdomain.ch:80
$ sudo azcmagent_proxy add http://proxy.yourdomain.ch:80Preparing Microsoft Defender/ Arc for SLES/ SUSE
# Jump to your home folder
$ cd
# Download the official azure installation script for defender
$ curl -o mde_install.sh https://github.com/microsoft/mdatp-xplat/blob/master/linux/installation/mde_installer.sh
# In case your Linux server has no direct internet access you can use curl with a Proxy. Use -x:
curl -x http://proxy.yourdomain.ch:80 -o mde_install.sh https://github.com/microsoft/mdatp-xplat/blob/master/linux/installation/mde_installer.sh
# Add the official repository for the defender and arc packages
$ sudo zypper addrepo -c -f -n microsoft-prod https://packages.microsoft.com/config/sles/15/prod.repo
# Trust the repositories by accepting the GPG key after the zypper refresh
$ sudo zypper refresh
# Install both packages
$ sudo zypper install mdatp azcmagent
# Add a proxy to both the mdatp (Defender) and azcmagent (ARC)
$ sudo mdatp config proxy set --value http://proxy.yourdomain.ch:80
$ sudo azcmagent_proxy add http://proxy.yourdomain.ch:80Preparing Microsoft Defender/ Arc for Debian
# Jump to your home folder
$ cd
# Download the official azure installation script for defender
curl -o mde_install.sh https://github.com/microsoft/mdatp-xplat/blob/master/linux/installation/mde_installer.sh
# In case your Linux server has no direct internet access you can use curl with a Proxy. Use -x:
$ curl -x http://proxy.yourdomain.ch:80 -o mde_install.sh https://github.com/microsoft/mdatp-xplat/blob/master/linux/installation/mde_installer.sh
# Install dependencies which will be needed for the process
$ sudo apt-get install curl libplist-utils gpg gnupg apt-transport-https
# Add the new Repositories to your server
$ curl -o microsoft.list https://packages.microsoft.com/config/debian/12/prod.list
# Move the new repo-file to the apt repository folder
$ sudo mv microsoft.list /etc/apt/sources.list.d/microsoft-prod.list
# Download and import the GPG key for the new repositories via proxy:
$ curl -x http://proxy.yourdomain.ch:80 -sSL https://packages.microsoft.com/keys/microsoft.asc | gpg --dearmor | sudo tee /usr/share/keyrings/microsoft-prod.gpg > /dev/null
# Refresh all repositories
$ sudo apt update
# Install both packages
$ sudo apt-get install mdatp azcmagent
# Add a proxy to both the mdatp (Defender) and azcmagent (ARC)
$ sudo mdatp config proxy set --value http://proxy.yourdomain.ch:80
$ sudo azcmagent_proxy add http://proxy.yourdomain.ch:80Preparing Microsoft Defender/ Arc for Ubuntu
# Jump to your home folder
$ cd
# Download the official azure installation script for defender
curl -o mde_install.sh https://github.com/microsoft/mdatp-xplat/blob/master/linux/installation/mde_installer.sh
# In case your Linux server has no direct internet access you can use curl with a Proxy. Use -x:
$ curl -x http://proxy.yourdomain.ch:80 -o mde_install.sh https://github.com/microsoft/mdatp-xplat/blob/master/linux/installation/mde_installer.sh
# Install dependencies which will be needed for the process
$ sudo apt-get install curl libplist-utils gpg gnupg apt-transport-https
# Add the new GPG-Key to your server and install it
$ curl https://packages.microsoft.com/keys/microsoft.asc | gpg --dearmor > microsoft.gpg
$ sudo install -o root -g root -m 644 microsoft.gpg /usr/share/keyrings/
rm microsoft.gpg
# Create a new Repository file and update your apt package manager
$ sudo sh -c 'echo "deb [arch=amd64 signed-by=/usr/share/keyrings/microsoft.gpg] https://packages.microsoft.com/ubuntu/$(lsb_release -rs)/prod $(lsb_release -cs) main" >> /etc/apt/sources.list.d/microsoft-ubuntu-$(lsb_release -cs)-prod.list'
# Refresh all repositories
$ sudo apt update
# Install both packages
$ sudo apt-get install mdatp azcmagent
# Add a proxy to both the mdatp (Defender) and azcmagent (ARC)
$ sudo mdatp config proxy set --value http://proxy.yourdomain.ch:80
$ sudo azcmagent_proxy add http://proxy.yourdomain.ch:80Setup/ Configure Defender/ Arc on all Distributions
# Make sure the Azure script has access to be executed
$ sudo chmod +x mde_installer.sh
# Execute the Azure script with your generated Onboarding script
$ sudo ./mde_installer.sh -o WindowsDefenderATPOnboardingPackage.py
# This step shall return a state “Onboarded”
# We can now additionally activate the real time protection
$ sudo mdatp config real-time-protection --value enabled
# One can check the health of the setup with running
$ sudo mdatp health
# Now we can add the Linux server to the ARC
$ sudo azcmagent connect -l switzerlandnorth -s <SubscriptionID> -g <GroupPolicy>
# This step will return a webpage on your Azure including a unique key which we need to type in into the login prompt. This can only be done if your account ahs sufficient rights to maintain and add new clients to your organizations AzureSummary & Hints
This technical guide will help you connect any Linux server to your existing Azure Defender and Arc portal. Once set up, you’ll unlock some great benefits for securing your systems. Here’s what you get:
- Real-time threat protection: Defender instantly scans files for malware, viruses, or other threats as they pop up on your Linux servers.
- Cross-platform support: It works seamlessly with Windows, macOS, and more, so you can manage all devices from one place.
- Advanced threat detection: In addition, it uses smart cloud analytics to spot serious threats like ransomware or sneaky zero-day attacks.
- Vulnerability checks: Finds weak spots in your Linux setup, like outdated apps or bad configs, and suggests fixes.
- Centralized management: Furthermore, you can control all your Linux servers from the Defender portal, making updates and monitoring a breeze.
- Easier compliance: Helps meet strict security standards (like Cyber Essentials) with built-in tools for Linux environments.
It may take a bit for your newly added Linux machines to appear in the Defender and Arc Azure Portal. Depending on your data center’s location, it could take up to half a day for the portal to fully sync and display all your Linux systems’ details.
![Thumbnail [60x60]](https://www.dbi-services.com/blog/wp-content/uploads/2022/05/open-source-author.png)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/ADE_WEB-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2025/11/LTO_WEB.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2025/05/martin_bracher_2048x1536.jpg)